Security News > 2022 > September > Prynt Stealer Contains a Backdoor to Steal Victims' Data Stolen by Other Cybercriminals
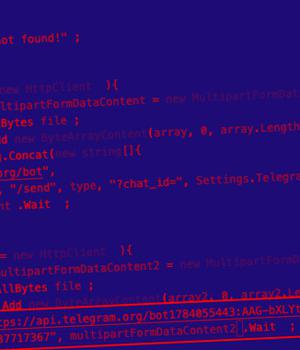
Researchers discovered a private Telegram channel-based backdoor in the information stealing malware, dubbed Prynt Stealer, which its developer added with the intention of secretly stealing a copy of victims' exfiltrated data when used by other cybercriminals.
Prynt Stealer, which came to light earlier this April, comes with capabilities to log keystrokes, steal credentials from web browsers, and siphon data from Discord and Telegram.
The cybersecurity firm analysis of Prynt Stealer shows that its codebase is derived from two other open source malware families, AsyncRAT and StormKitty, with new additions incorporated to include a backdoor Telegram channel to collect the information stolen by other actors to the malware's author.
While bad actors have employed similar data stealing tactics in the past where the malware is given away for free, the development marks one of the rare instances where a stealer that's sold on a subscription basis is also sending the plundered information back to its developer.
Zscaler said it identified two more variants of Prynt Stealer variants dubbed WorldWind and DarkEye written by the same author, the latter of which is bundled as an implant with a "Free" Prynt Stealer builder.
"The Prynt Stealer author went a step further and added a backdoor to steal from their customers by hardcoding a Telegram token and chat ID into the malware. As the saying goes, there is no honor among thieves."
News URL
https://thehackernews.com/2022/09/prynt-stealer-contains-backdoor-to.html