Security News > 2022 > September > JuiceLedger Hackers Behind the Recent Phishing Attacks Against PyPI Users
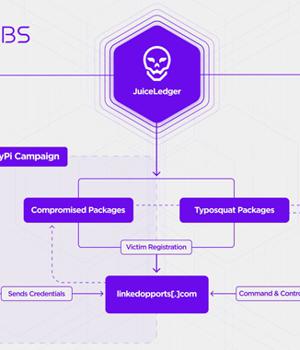
More details have emerged about the operators behind the first-known phishing campaign specifically aimed at the Python Package Index, the official third-party software repository for the programming language.
The attacks received a significant facelift last month when the JuiceLedger actors targeted PyPi package contributors in a phishing campaign, resulting in the compromise of three packages with malware.
"The supply chain attack on PyPI package contributors appears to be an escalation of a campaign begun earlier in the year which initially targeted potential victims through fake cryptocurrency trading applications," SentinelOne researcher Amitai Ben Shushan Ehrlich said in a report.
The goal is presumably to infect a wider audience with the infostealer through a mix of trojanized and typosquat packages, the cybersecurity firm added.
With account takeover attacks becoming a popular infection vector for attackers looking to poison software supply chains, PyPI has begun imposing a mandatory two-factor authentication requirement for projects deemed "Critical."
"JuiceLedger appears to have evolved very quickly from opportunistic, small-scale infections only a few months ago to conducting a supply chain attack on a major software distributor," SentinelOne said.
News URL
https://thehackernews.com/2022/09/juiceledger-hackers-behind-recent.html
Related news
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Hackers Repurpose RansomHub's EDRKillShifter in Medusa, BianLian, and Play Attacks (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks (source)
- Russian hackers attack Western military mission using malicious drive (source)
- iOS devices face twice the phishing attacks of Android (source)
- Windows NTLM hash leak flaw exploited in phishing attacks on governments (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)