Security News > 2022 > June > Technical Details Released for 'SynLapse' RCE Vulnerability Reported in Microsoft Azure
Microsoft has incorporated additional improvements to address the recently disclosed SynLapse security vulnerability in order to meet comprehensive tenant isolation requirements in Azure Data Factory and Azure Synapse Pipelines.
The high-severity issue, tracked as CVE-2022-29972 and disclosed early last month, could have allowed an attacker to perform remote command execution and gain access to another Azure client's cloud environment.
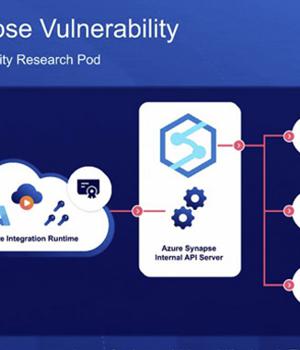
"SynLapse enabled attackers to access Synapse resources belonging to other customers via an internal Azure API server managing the integration runtimes," the researchers said.
Besides permitting an attacker to obtain credentials to other Azure Synapse customer accounts, the flaw made it possible to sidestep tenant separation and execute code on targeted customer machines as well as control Synapse workspaces and leak sensitive data to other external sources.
At its core, the issue relates to a case of command injection found in the Magnitude Simba Amazon Redshift ODBC connector used in Azure Synapse Pipelines that could be exploited to achieve code execution a user's integration runtime, or on the shared integration runtime.
"More specifically, the fact that given an RCE on the shared integration runtime let us use a client certificate providing access to a powerful, internal API server. This enabled an attacker to compromise the service and access other customers' resources."
News URL
https://thehackernews.com/2022/06/technical-details-released-for-synlapse.html
Related news
- Critical PHP RCE vulnerability mass exploited in new attacks (source)
- Critical Veeam Backup & Replication RCE vulnerability fixed, patch ASAP! (CVE-2025-23120) (source)
- Infoseccers criticize Veeam over critical RCE vulnerability and a failing blacklist (source)
- Critical Ingress NGINX Controller Vulnerability Allows RCE Without Authentication (source)
- Ivanti VPN customers targeted via unrecognized RCE vulnerability (CVE-2025-22457) (source)
- Microsoft Patches 125 Flaws Including Actively Exploited Windows CLFS Vulnerability (source)
- CISA Warns of CentreStack's Hard-Coded MachineKey Vulnerability Enabling RCE Attacks (source)
- Microsoft: Windows CLFS Vulnerability Could Lead to ‘Widespread Deployment and Detonation of Ransomware’ (source)
- Gladinet’s Triofox and CentreStack Under Active Exploitation via Critical RCE Vulnerability (source)
- Microsoft Secures MSA Signing with Azure Confidential VMs Following Storm-0558 Breach (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2022-05-09 | CVE-2022-29972 | Argument Injection or Modification vulnerability in Insightsoftware Magnitude Simba Amazon Redshift Odbc Driver An argument injection vulnerability in the browser-based authentication component of the Magnitude Simba Amazon Redshift ODBC Driver (1.4.14 through 1.4.21.1001 and 1.4.22 through 1.4.x before 1.4.52) may allow a local user to execute arbitrary code. | 7.8 |