Security News > 2022 > May > Hackers Deploy IceApple Exploitation Framework on Hacked MS Exchange Servers
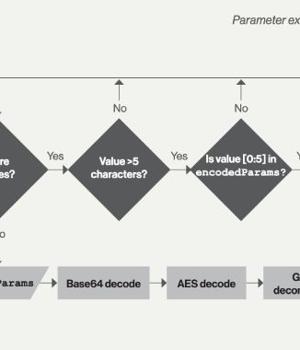
NET-based post-exploitation framework called IceApple that has been deployed on Microsoft Exchange server instances to facilitate reconnaissance and data exfiltration.
"Suspected to be the work of a state-nexus adversary, IceApple remains under active development, with 18 modules observed in use across a number of enterprise environments, as of May 2022," CrowdStrike said in a Wednesday report.
IceApple is notable for the fact that it's an in-memory framework, indicating an attempt on the part of the threat actor to maintain a low forensic footprint and evade detection, which, in turn, bears all hallmarks of a long-term intelligence-gathering mission.
While intrusions observed so far have involved the malware being loaded on Microsoft Exchange Servers, IceApple is capable of running under any Internet Information Services web application, making it a potent threat.
"At its core, IceApple is a post-exploitation framework focused on increasing an adversary's visibility of a target through acquisition of credentials and exfiltration of data," the researchers concluded.
"IceApple has been developed by an adversary with detailed knowledge of the inner workings of IIS. Ensuring all web applications are regularly and fully patched is critical to preventing IceApple from ending up in your environment."
News URL
https://thehackernews.com/2022/05/hackers-deploy-iceapple-exploitation.html
Related news
- Oracle says "obsolete servers" hacked, denies cloud breach (source)
- ASUS releases fix for AMI bug that lets hackers brick servers (source)
- Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised (source)
- Germany takes down eXch cryptocurrency exchange, seizes servers (source)
- Chinese hackers behind attacks targeting SAP NetWeaver servers (source)
- Türkiye Hackers Exploited Output Messenger Zero-Day to Drop Golang Backdoors on Kurdish Servers (source)
- Russia-linked hackers target webmail servers in Ukraine-related espionage operation (source)