Security News > 2022 > February > Moses Staff Hackers Targeting Israeli Organizations for Cyber Espionage
The politically motivated Moses Staff hacker group has been observed using a custom multi-component toolset with the goal of carrying out espionage against its targets as part of a new campaign that exclusively singles out Israeli organizations.
First publicly documented in late 2021, Moses Staff is believed to be sponsored by the Iranian government, with attacks reported against entities in Israel, Italy, India, Germany, Chile, Turkey, the U.A.E., and the U.S. Earlier this month, the hacker collective was observed incorporating a previously undocumented remote access trojan called "StrifeWater" that masquerades as the Windows Calculator app to evade detection.
The latest threat activity involves an attack path that leverages the ProxyShell vulnerability in Microsoft Exchange servers as an initial infection vector to deploy two web shells, followed by exfiltrating Outlook Data Files from the compromised server.
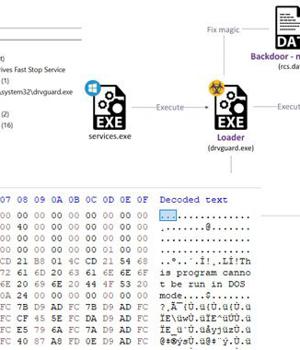
The installation of the "Broker" implant, which is used to execute commands fetched from a remote server, download files, and exfiltrate data from target networks, is facilitated by a loader that masquerades as a "Hard Disk Drives Fast Stop Service" dubbed "DriveGuard".
The attribution to Moses Staff is based on similarities in the web shells used in previously disclosed attacks and its pattern of victimology.
"The group is highly motivated, capable, and set on damaging Israeli entities," the researchers said.
News URL
https://thehackernews.com/2022/02/moses-staff-hackers-targeting-israeli.html