Security News

Microsoft is adding a new Canary channel to its nine-year-old Windows Insider Program to let the most fearless users test what it describes as "Hot off the presses" features. Windows builds released through the Canary Channel will have higher numbers than the ones in the Dev, Beta, and Release Preview channels, starting with 25000 series builds.

The seemingly innocuous Microsoft OneNote file has become a popular file format used by hackers to spread malware and breach corporate networks. To give a little background on how we got to Microsoft OneNote files becoming the tool of choice for malware-distributing phishing attacks, we first need to explain how we got here.

Microsoft is testing a new and modern-looking Windows 11 volume mixer accessible via the taskbar Quick Settings panel that helps adjust the volume on a per-app basis and switch between audio devices. Testers need to open the Quick Settings panel to access it after clicking the volume icon in the Windows tray or use the new global keyboard shortcut for even faster control.

Microsoft has released out-of-band security updates for 'Memory Mapped I/O Stale Data' information disclosure vulnerabilities in Intel CPUs.The Mapped I/O side-channel vulnerabilities were initially disclosed by Intel on June 14th, 2022, warning that the flaws could allow processes running in a virtual machine to access data from another virtual machine.

The developers of the BlackLotus UEFI bootkit have improved the malware with Secure Boot bypass capabilities that allow it to infected even fully patched Windows 11 systems. BlackLotus is the first public example of UEFI malware that can avoid the Secure Boot mechanism, thus being able to disable security protections that come with the operating system.

ESET researchers have published the first analysis of a UEFI bootkit capable of circumventing UEFI Secure Boot, a critical platform security feature. "Our investigation started with a few hits on what turned out to be the BlackLotus user-mode component - an HTTP downloader - in our telemetry late in 2022. After an initial assessment, code patterns found in the samples brought us to the discovery of six BlackLotus installers. This allowed us to explore the whole execution chain and to realize that what we were dealing with here is not just regular malware," says Martin Smolár, the ESET researcher who led the investigation into the bootkit.

BlackLotus, a UEFI bootkit that's sold on hacking forums for about $5,000, can now bypass Secure Boot, making it the first known malware to run on Windows systems even with the firmware security feature enabled. Secure Boot is supposed to prevent devices from running unauthorized software on Microsoft machines.
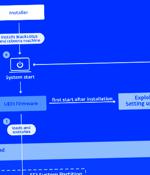
A stealthy Unified Extensible Firmware Interface bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot defenses, making it a potent threat in the cyber landscape. "This bootkit can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled," Slovak cybersecurity company ESET said in a report shared with The Hacker News.

Cybercriminals are disguising the PlugX remote access trojan as a legitimate open-source Windows debugging tool to evade detection and compromise systems. In a recent case detailed by Trend Micro, miscreants used a PlugX variant to hijack the popular x64dbg debugging tool to go undetected.

Microsoft says the KB5022913 February 2023 non-security preview release is incompatible with some third-party UI customization apps and is causing boot issues on Windows 11 22H2 systems. In a new update to the Windows Health Dashboard, the company explained that using third-party UI customization applications could potentially prevent Windows from starting up properly.