Security News

Microsoft has officially released Windows 11 and ISO images that allow you to create bootable media to perform clean installs of the operating system and troubleshoot bugs and problems. Go to Download Windows 11 page in your favorite web browser.

Microsoft has released Windows 11 worldwide, and it is now rolling it out via Windows Update on devices with compatible hardware and the latest updates. Windows 10 users can upgrade to Windows 11 for free now via Windows Update as long as their device has compatible hardware.
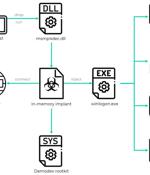
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems. Attacks mounted by the hacking group, dubbed GhostEmperor by Kaspersky, are also said to have used a "Sophisticated multi-stage malware framework" that allows for providing persistence and remote control over the targeted hosts.

Microsoft has released the optional KB5005611 Preview cumulative update for Windows 10 2004, Windows 10 20H2, and Windows 10 21H1. This update fixes bugs in Microsoft Outlook and makes it easier to mitigate the PrintNightmare vulnerability. This cumulative update is part of Microsoft's September 2021 monthly "C" update, allowing Windows users to test the upcoming fixes before they are automatically deployed in the forthcoming October 2021 Patch Tuesday.

Threat actors are trying to capitalize on the recent revelations on Pegasus spyware from Amnesty International to drop a less-known remote access tool called Sarwent. The malware looks and acts the part of a legitimate antivirus solution specially created to scan the system for traces of Pegasus traces and to remove them.

The latest version of the long-term support release of Windows Server, Windows Server 2022, is now available. Windows Server 2022 is the new long-term servicing channel release of Windows Server for on-premises data centers and virtual machines.

Chinese-speaking cyberspies have targeted Southeast Asian governmental entities and telecommunication companies for more than a year, backdooring systems running the latest Windows 10 versions with a newly discovered rootkit. The hacking group, dubbed GhostEmperor by Kaspersky researchers who spotted it, use the Demodex rootkit, which acts as a backdoor to maintain persistence on compromised servers.
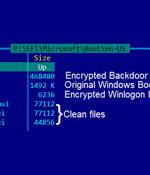
Commercially developed FinFisher surveillanceware has been upgraded to infect Windows devices using a UEFI bootkit using a trojanized Windows Boot Manager, marking a shift in infection vectors that allow it to elude discovery and analysis. While the tool was previously deployed through tampered installers of legitimate applications such as TeamViewer, VLC, and WinRAR that were backdoored with an obfuscated downloader, subsequent updates in 2014 enabled infections via Master Boot Record bootkits with the goal of injecting a malicious loader in a manner that's engineered to slip past security tools.

Microsoft is relaxing its app store policies for Windows and the redesigned marketplace will meet the needs of customers and developers across a variety of app experiences. With Windows 11, Microsoft has opened up its store to developers using different types of frameworks, packaging technologies, and commerce platforms.

Commercially developed FinFisher malware now can infect Windows devices using a UEFI bootkit that it injects in the Windows Boot Manager. "During our research, we found a UEFI bootkit that was loading FinSpy. All machines infected with the UEFI bootkit had the Windows Boot Manager replaced with a malicious one," Kasperksy researchers revealed today.