Security News

Boucher and Anderson discovered that they can be misused to misrepresent source code. "Our key insight is that we can reorder source code characters in such a way that the resulting display order also represents syntactically valid source code."

Named "Trojan Source attacks," the method "Exploits subtleties in text-encoding standards such as Unicode to produce source code whose tokens are logically encoded in a different order from the one in which they are displayed, leading to vulnerabilities that cannot be perceived directly by human code reviewers," Cambridge University researchers Nicholas Boucher and Ross Anderson said in a paper published on Monday. The researchers have coordinated disclosure with 19 organizations, many of which are now releasing updates to address the security weakness in code compilers, interpreters, code editors and repositories.

A malware peddler has created a fake website posing as Amnesty International to serve gullible marks with software that claims to protect users against NSO Group's Pegasus malware. Trading on fears about the Pegasus malware, this development takes the usual evolution of malware download lures and picks a particularly nasty vector, preying on those looking for protection against advanced threats.

Mobile security firm Zimperium, which first identified the GriftHorse Android Trojan, says the malware has infected more than 10 million Android devices worldwide; a fraction of one per cent of active 'droid devices, but still misery for literally millions of people. In a blog post on Wednesday, Zimperium researchers Aazim Yaswant and Nipun Gupta said that Trojan code dubbed GriftHorse has been spotted in more than 200 malicious apps in at least 70 different countries and has been afflicting Android phones since November 2020.

A newly discovered "Aggressive" mobile campaign has infected north of 10 million users from over 70 countries via seemingly innocuous Android apps that subscribe the individuals to premium services costing €36 per month without their knowledge. Zimperium zLabs dubbed the malicious trojan "GriftHorse." The money-making scheme is believed to have been under active development starting from November 2020, with victims reported across Australia, Brazil, Canada, China, France, Germany, India, Russia, Saudi Arabia, Spain, the U.K., and the U.S. No fewer than 200 trojan applications were used in the campaign, making it one of the most widespread scams to have been uncovered in 2021.

More than 10 million Android users have been saddled with a malware called GriftHorse that's trojanizing various applications and secretly subscribing victims to premium mobile services - a type of billing fraud that researchers categorize as "Fleeceware." Zimperium uncovered more than 130 GriftHorse apps being distributed through both Google Play and third-party application stores, across all categories.

A new advanced trojan sold on Russian-speaking underground forums comes with capabilities to steal users' accounts on popular online video game distribution services, including Steam, Epic Games Store, and EA Origin, underscoring a growing threat to the lucrative gaming market. The information harvested from gaming apps, such as Bethesda, Epic Games, GOG, Origin, Steam, and VimeWorld, is exfiltrated to a remote server, from where it's likely to be monetized on darknet platforms or Telegram channels that are dedicated to selling access to online gaming accounts.

A newly spotted banking trojan has been caught leveraging legitimate platforms like YouTube and Pastebin to store its encrypted, remote configuration and commandeer infected Windows systems, making it the latest to join the long list of malware targeting Latin America after Guildma, Javali, Melcoz, Grandoreiro, Mekotio, Casbaneiro, Amavaldo, Vadokrist, and Janeleiro. " interesting new techniques to the pool of Latin American banking trojans' tricks, like using seemingly useless ZIP archives or bundling payloads with decoy BMP images," ESET researchers said in a technical analysis published on Friday.

A new Android banking trojan named SOVA is under active development, researchers said, and it has big dreams even in its infancy stage. "Regarding the development, SOVA also stands out for being fully developed in Kotlin, a coding language supported by Android and thought by many to be the future of Android development," according to ThreatFabric.
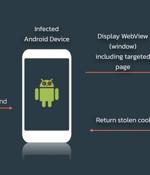
A mix of banking applications, cryptocurrency wallets, and shopping apps from the U.S. and Spain are the target of a newly discovered Android trojan that could enable attackers to siphon personally identifiable information from infected devices, including banking credentials and open the door for on-device fraud. Dubbed S.O.V.A., the current version of the banking malware comes with myriad features to steal credentials and session cookies through web overlay attacks, log keystrokes, hide notifications, and manipulate the clipboard to insert modified cryptocurrency wallet addresses, with future plans to incorporate on-device fraud through VNC, carry out DDoS attacks, deploy ransomware, and even intercept two-factor authentication codes.