Security News
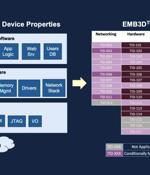
The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments. "The model provides a...

Review and manage your consent Here's an overview of our use of cookies, similar technologies and how to manage them. You can also change your choices at any time, by hitting the "Your Consent Options" link on the site's footer.

Review and manage your consent Here's an overview of our use of cookies, similar technologies and how to manage them. You can also change your choices at any time, by hitting the "Your Consent Options" link on the site's footer.

The importance of software threat modeling continues to grow. NIST advises software engineers to adhere to secure software development best practices and do software threat modeling repeatedly during the development process, especially when creating new capabilities.

Many experts attempt to use traditional threat modeling as their first line of business to address security in the SDLC. But what if everyone is doing threat modeling wrong? The industry standard for how we conduct threat modeling today evolved from past meetings where security professionals piled into a conference room and brainstormed potential threats that might affect their software.

Security Compass published the results of a report designed to provide a better understanding of the current state of threat modeling in mid-sized, $100M to $999M and large sized, $1B + enterprises, with a specific focus on the challenges organizations face in scaling threat modeling for the applications they build and deploy. Current performance on threat modeling approaches Only 25% of survey participants indicate their organizations conduct threat modeling during the early phases of software development requirements gathering and design, before proceeding with application development.

Organizations need to rethink their approach to threat modeling or risk losing its value as a key defense in their cybersecurity arsenals. The traditional approaches to threat modeling can be very effective, but they don't scale well enough in the current computing and threat landscape.

QNAP NAS devices under ransomware attackQNAP NAS device owners are once again under attack by ransomware operators, who are exploiting a recently fixed vulnerability to lock data on vulnerable devices by using the 7-Zip open-source file archiver utility. Q1 2021 ransomware trends: Most attacks involved threat to leak stolen dataThe vast majority of ransomware attacks now include the theft of corporate data, Coveware says, but victims of data exfiltration extortion have very little to gain by paying a cyber criminal.

While there is not one exact industry wide definition, threat modeling can be summarized as a practice to proactively analyze the cyber security posture of a system or system of systems. In short, threat modeling answers questions as "Where am I most vulnerable to attacks?", "What are the key risks?", and "What should I do to reduce these risks?".

Fouad Khalil of SecurityScorecard on a Dynamic ApproachApplication threat modeling enables the systematic evaluation of applications from an attacker's point of view, says Fouad Khalil of...