Security News

The data wiping malware called AcidPour may have been deployed in attacks targeting four telecom providers in Ukraine, new findings from SentinelOne show. The cybersecurity firm also confirmed...

A former manager at a telecommunications company in New Jersey pleaded guilty to conspiracy charges for accepting money to perform unauthorized SIM swaps that enabled an accomplice to hack customer accounts. SIM swapping is an unauthorized porting of a targeted person's phone number to another physical SIM card or eSIM chip controlled by the attacker.
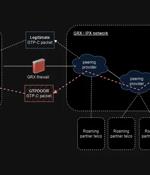
Threat hunters have discovered a new Linux malware called GTPDOOR that’s designed to be deployed in telecom networks that are adjacent to GPRS roaming exchanges (GRX) The malware is novel in the...

Starting March 13th, telecommunications companies must report data breaches impacting customers' personally identifiable information within 30 days, as required by FCC's updated data breach reporting requirements."Without an FCC rule requiring breach notifications for the above categories of PII, there would be no requirement in Federal law that telecommunications carriers report non-CPNI breaches to their customers," the FCC said.

Telecommunication, media, internet service providers (ISPs), information technology (IT)-service providers, and Kurdish websites in the Netherlands have been targeted as part of a new cyber...

Ukrainian cybersecurity authorities have disclosed that the Russian state-sponsored threat actor known as Sandworm was inside telecom operator Kyivstar's systems at least since May 2023. The...

The Assembly of the Republic of Albania and telecom company One Albania have been targeted by cyber attacks, the country’s National Authority for Electronic Certification and Cyber Security...

The Iranian nation-state actor known as MuddyWater has leveraged a newly discovered command-and-control (C2) framework called MuddyC2Go in its attacks on the telecommunications sector in Egypt,...

Ukraine's biggest telecom operator Kyivstar has become the victim of a cyber attack, disrupting customer access to mobile and internet services. "The cyberattack on Ukraine's #Kyivstar telecoms...

A previously unknown Linux remote access trojan called Krasue has been observed targeting telecom companies in Thailand by threat actors to main covert access to victim networks at lease since...