Security News

Microsoft has addressed an Azure Active Directory authentication flaw that could allow threat actors to escalate privileges and potentially fully take over the target's account. This misconfiguration could be abused in account and privilege escalation attacks against Azure AD OAuth applications configured to use the email claim from access tokens for authorization.
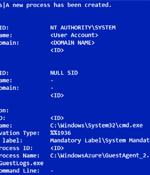
A financially motivated cyber actor has been observed abusing Microsoft Azure Serial Console on virtual machines to install third-party remote management tools within compromised environments. "This method of attack was unique in that it avoided many of the traditional detection methods employed within Azure and provided the attacker with full administrative access to the VM," the threat intelligence firm said.

WhatsApp will be rolling out three new security features in the coming months, to provide users with increased privacy and control over their messages and to help prevent unauthorized account access and takeover. WhatsApp's new check when moving account to another phone.
"Mobile device malware is one of the biggest threats to people's privacy and security today because it can take advantage of your phone without your permission and use your WhatsApp to send unwanted messages," the Meta-owned company said in an announcement. Called Device Verification, the security measure is designed to help prevent account takeover attacks by blocking the threat actor's connection and allowing the target to use the app without any interruption.

WhatsApp announced today the introduction of several new security features, one of them dubbed "Device Verification" and designed to provide better protection against account takeover attacks. Device Verification prevents malware from using authentication keys stolen from infected mobile devices or via unofficial clients to impersonate accounts and use them to send scam and phishing messages to people in the targeted users' contact lists.

A stranger may be receiving your private WhatsApp messages, and also be able to send messages to all of your contacts - if you have changed your phone number and didn't delete the WhatsApp account linked to it. "If for some reason you no longer want to use WhatsApp tied to a particular phone number, then the best thing to do is transfer it to a new phone number or delete the account within the app."

Security researchers have disclosed multiple architectural vulnerabilities in Siemens SIMATIC and SIPLUS S7-1500 programmable logic controllers that could be exploited by a malicious actor to stealthily install firmware on affected devices and take control of them. Put differently, the weaknesses are the result of a lack of asymmetric signature verifications for firmware at bootup, effectively permitting the attacker to load tainted bootloader and firmware while undermining integrity protections.

Enterprising cybercriminals don't have to work very hard to gain access to your network and all the valuable information stored inside it. That's because employee accounts are so easy to hack.

Nvidia fixed more than two dozen security flaws in its GPU display driver, the most severe of which could allow an unprivileged user to modify files, and then escalate privileges, execute code, tamper with or steal data, or even take over your device. In total, the chipmaker patched 29 vulnerabilities affecting Windows and Linux products, including 10 high-severity bugs.

You will also receive a complimentary subscription to TechRepublic's News and Special Offers newsletter and the Top Story of the Day newsletter. You may unsubscribe from these newsletters at any time.