Security News

This picture comes from the Ukraine Cyber Police, who raided a fraudulent call centre just before New Year, where they say the three founders of the scam, plus 37 "Staff", were busted for allegedly operating a large-scale banking fraud. Typically, the scammers try to convince you that your bank account is under attack from fraudsters, and patiently offer to help you "Secure" your account and "Recover" lost or at-risk funds.
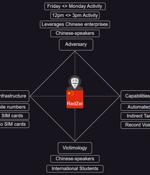
Chinese international students in the U.K. have been targeted by persistent Chinese-speaking scammers for over a year as part of an activity dubbed RedZei. The most notable aspect about the operation is the steps taken by the threat actors to bypass steps taken by users to prevent scam calls, using a new pay-as-you-go U.K. phone number for each wave so as to render phone number-based blocking ineffective.
If you follow this advice, you might jump to the dangerous conclusion that the site must surely know your real password, and must therefore be genuine, given that it seems to know that you put in the wrong password. Of course, the crooks can safely pretend you got your password wrong the first time, even if you didn't.

OneCoin appeared to be what's known as a pyramid scheme, or MLM system, short for multi-level marketing, where the people who buy in at the start earn commission for bringing in the next wave of "Investors", who in turn earn commission from bringing in the third wave, and so on. OneCoin falsely claimed that the value of OneCoin was based on market supply and demand, when in fact, the value of the cryptocurrency was simply set by OneCoin itself.

In this Help Net Security video, Ronnie Tokazowski, Principal Threat Advisor at Cofense, offers insight into the world's most lucrative cybercrime - business email compromise. The Cofense team recently purchased $500 worth of trackable gift cards to intentionally give to scammers in the hopes of discovering what happens once scammers receive these funds, engaging with 54 live BEC attacks over 5 weeks.

A vulnerability in popular remote access service/platform ConnectWise Control could have been leveraged by scammers to make compromising targets' computers easier, Guardio researchers have discovered. By abusing the fully-featured 14-day trial option for that hosted cloud service, scammers are already taking advantage of the platform at no cost, but the vulnerability could have allowed them to remove an alert that can break the illusion the scammers are trying to create.

At which point the crooks immediately try to use the combination of username + password + one-time code they just got hold of, in the hope of logging in quickly enough to get into your account before you realise there's anything phishy going on. As a result, social media users are understandably concerned about protecting their accounts in general, whether they're specifically concerned about Twitter or not: Lure you to a real page with a facebook.com URL. The account is fake, set up entirely for this particular scam campaign, but the link that shows up in the email you receive does indeed lead to facebook.com, making it less likely to attract suspicion, either from you or from your spam filter.

An open ben, or "Open beneficiary", is explained by the investigator as "An account where a different business account name can be substituted to help in deceiving the victim into sending funds." Presumably, the money launderer's contacts - other cogs in the cybercrime gearbox who send out so-called money mules to open accounts that are later used for fraud - were pushing back against the "Cost" of going through face-to-face KYC checks to open accounts that ended up getting linked to criminality right away.

The FBI warns that tech support scammers are now impersonating financial institutions' refund payment portals to harvest victims' sensitive information and add legitimacy. "Within the body of the email, the scammers will indicate the specific service to be renewed with a price commonly in the range of $300 to $500 USD, provoking a sense of urgency in the victims to contact them and provide information for a refund," the FBI said.

The FBI has released a warning that scammers may be targeting individuals seeking to enroll in the Federal Student Aid program to steal their personal information, payment details, and money. Federal Student Aid is a debt relief program announced in August 2022 that opened for applications yesterday.