Security News

Cybersecurity researchers are calling attention to a new Linux cryptojacking campaign that's targeting publicly accessible Redis servers. The malicious activity has been codenamed RedisRaider by...

P2PInfect, originally a dormant peer-to-peer malware botnet with unclear motives, has finally come alive to deploy a ransomware module and a cryptominer in attacks on Redis servers. P2PInfect was first documented in July 2023 by Unit 42 researchers, targeting Redis servers using known vulnerabilities.

Threat actors are targeting misconfigured and vulnerable servers running Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services as part of an emerging malware campaign designed to...

Hackers are targeting misconfigured servers running Apache Hadoop YARN, Docker, Confluence, or Redis with new Golang-based malware that automates the discovery and compromise of the hosts. According to the researchers, the hackers deploy a set of four novel Golang payloads that are responsible for identifying and exploiting hosts running services for Hadoop YARN, Docker, Confluence, and Redis.

Security researchers discovered a new campaign that targets Redis servers on Linux hosts using a piece of malware called 'Migo' to mine for cryptocurrency. Hackers are always looking for exposed and potentially vulnerable Redis servers to hijack resources, steal data, and other malicious purposes.

A novel malware campaign has been observed targeting Redis servers for initial access with the ultimate goal of mining cryptocurrency on compromised Linux hosts. "This particular campaign involves...

Cybersecurity researchers have detailed an updated version of the malware HeadCrab that's known to target Redis database servers across the world since early September 2021. The development, which...
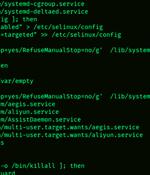
Vulnerable Redis services have been targeted by a "New, improved, dangerous" variant of a malware called SkidMap that's engineered to target a wide range of Linux distributions. "The malicious nature of this malware is to adapt to the system on which it is executed," Trustwave security researcher Radoslaw Zdonczyk said in an analysis published last week.

Threat actors are actively targeting exposed instances of SSH and Redis Redis open-source data store with a peer-to-peer self-replicating worm with versions for both Windows and Linux that the malware authors named P2Pinfect. After compromising a vulnerable Redis instance with an initial payload, P2PInfect downloads new OS-specific scripts and malicious binaries and adds the server to its list of infected systems.
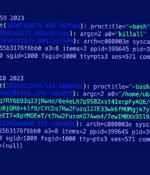
The P2PInfect peer-to-peer worm has been observed employing previously undocumented initial access methods to breach susceptible Redis servers and rope them into a botnet. "The malware compromises exposed instances of the Redis data store by exploiting the replication feature," Cado Security researchers Nate Bill and Matt Muir said in a report shared with The Hacker News.