Security News

350,000 open source projects at risk from Python vulnerability. Cybersecurity company Trellix announced Wednesday that a known Python vulnerability puts 350,000 open-source projects and the applications that use them at risk of device take over or malicious code execution.
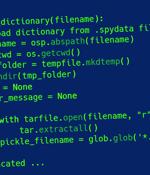
As many as 350,000 open source projects are believed to be potentially vulnerable to exploitation as a result of a security flaw in a Python module that has remained unpatched for 15 years. "The vulnerability is a path traversal attack in the extract and extractall functions in the tarfile module that allow an attacker to overwrite arbitrary files by adding the '.' sequence to filenames in a TAR archive," Trellix security researcher Kasimir Schulz said in a writeup.

Trellix Advanced Research Center published its research into CVE-2007-4559, a vulnerability estimated to be present in over 350,000 open-source projects and prevalent in closed-source projects.The vulnerability exists in the Python tarfile module which is a default module in any project using Python and is found extensively in frameworks created by Netflix, AWS, Intel, Facebook, Google, and applications used for machine learning, automation and docker containerization.

At least 350,000 open source projects are believed to be potentially vulnerable to exploitation via a Python module flaw that has remained unfixed for 15 years. Identified as CVE-2007-4559, the vulnerability surfaced on August 24, 2007, in a Python mailing list post from Jan Matejek, who was at the time the Python package maintainer for SUSE. It can be exploited to potentially overwrite and hijack files on a victim's machine, when a vulnerable application opens a malicious tar archive via tarfile.

A vulnerability in the Python programming language that has been overlooked for 15 years is now back in the spotlight as it likely affects more than 350,000 open-source repositories and can lead to code execution. The vulnerability is in the Python tarfile package, in code that uses un-sanitized tarfile.
In another finding that could expose developers to increased risk of a supply chain attack, it has emerged that nearly one-third of the packages in PyPI, the Python Package Index, trigger automatic code execution upon downloading them. "A worrying feature in pip/PyPI allows code to automatically run when developers are merely downloading a package," Checkmarx researcher Yehuda Gelb said in a technical report published this week.
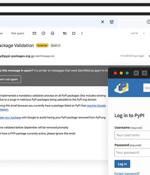
The Python Package Index, PyPI, on Wednesday sounded the alarm about an ongoing phishing campaign that aims to steal developer credentials and inject malicious updates to legitimate packages. "This is the first known phishing attack against PyPI," the maintainers of the official third-party software repository said in a series of tweets.

The operators of the XCSSET macOS malware have upped the stakes by making iterative improvements that add support for macOS Monterey by upgrading its source code components to Python 3. "The malware authors have changed from hiding the primary executable in a fake Xcode.app in the initial versions in 2020 to a fake Mail.app in 2021 and now to a fake Notes.app in 2022," SentinelOne researchers Phil Stokes and Dinesh Devadoss said in a report.
In what's yet another instance of malicious packages creeping into public code repositories, 10 modules have been removed from the Python Package Index for their ability to harvest critical data points such as passwords and Api tokens. The packages "Install info-stealers that enable attackers to steal developer's private data and personal credentials," Israeli cybersecurity firm Check Point said in a Monday report.

Without refactoring, a shift from Python 2.7 to Python 3.0 often means the code for Python 2.7 just doesn't work that well anymore, or even at all. Running existing code on an outdated version of Python avoids quite a lot of challenges because you don't need to refactor: you're keeping your code just the way it was.