Security News

Five malicious dropper Android apps with over 130,000 cumulative installations have been discovered on the Google Play Store distributing banking trojans like SharkBot and Vultur, which are capable of stealing financial data and performing on-device fraud. Targets of these droppers include 231 banking and cryptocurrency wallet apps from financial institutions in Italy, the U.K., Germany, Spain, Poland, Austria, the U.S., Australia, France, and the Netherlands.

Several adware apps promoted aggressively on Facebook as system cleaners and optimizers for Android devices are counting millions of installations on Google Play store. To evade deletion, the apps hide on the victim's device by constantly changing icons and names, masquerading as Settings or the Play Store itself.
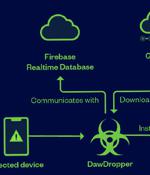
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware. These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others.

As many as 30 malicious Android apps with cumulative downloads of nearly 10 million have been found on the Google Play Store distributing adware. While masquerading as innocuous apps, their primary goal is to request permissions to show windows over other apps and run in the background in order to serve intrusive ads.

Google on Thursday said it's backtracking on a recent change that removed the app permissions list from the Google Play Store for Android across both the mobile app and the web. "We heard your feedback that you find the app permissions section in Google Play useful, and we've decided to reinstate it. The app permissions section will be back shortly."

Google has taken steps to ax dozens of fraudulent apps from the official Play Store that were spotted propagating Joker, Facestealer, and Coper malware families through the virtual marketplace. "Instead of waiting for apps to gain a specified volume of installs and reviews before swapping for a malware-laced version, the Joker developers have taken to hiding the malicious payload in a common asset file and package application using commercial packers," the researchers explained the new tactic adopted by the persistent malware to bypass detection.

Following the launch of a new "Data safety" section for the Android app on the Play Store, Google appears to be readying to remove the app permissions list from both the mobile app and the web. The Data safety section, which Google began rolling out in late April 2022, is the company's answer to Apple's Privacy Nutrition Labels in iOS, allowing users to have a unified view of an app's data collection and processing practices.

Cybersecurity researchers have discovered adware and information-stealing malware on the Google Play Store last month, with at least five still available and having amassed over two million downloads. Analysts at Dr. Web antivirus report that adware apps and data-stealing Trojans were among the most prominent Android threats in May 2022.

Another link discovered by Group-IB downloaded from Google Play, the official Android app store, a fake version of the 'Secure VPN' app, which is still present on Google Play at the time of writing and has just over 10 downloads. The researchers note that the description available for SideWinder's fake Secure VPN app has been copied from the legitimate NordVPN app.

More than 200 Android apps masquerading as fitness, photo editing, and puzzle apps have been observed distributing spyware called Facestealer to siphon user credentials and other valuable information. Facestealer, first documented by Doctor Web in July 2021, refers to a group of fraudulent apps that invade the official app marketplace for Android with the goal of plundering sensitive data such as Facebook login credentials.