Security News

A set of 15 high-severity security flaws have been disclosed in the CODESYS V3 software development kit that could result in remote code execution and denial-of-service under specific conditions, posing risks to operational technology environments. "Exploitation of the discovered vulnerabilities, which affect all versions of CODESYS V3 prior to version 3.5.19.0, could put operational technology infrastructure at risk of attacks, such as remote code execution and denial-of-service," Vladimir Tokarev of the Microsoft Threat Intelligence Community said in a report.

Still, most CISOs have made their mark securing IT environments - and IT security strategies and tools rarely translate to an OT context. While the soft skills of collaboration and team-building will certainly help CISOs as they bring the factory floor into their realm of responsibility, they must also make a concentrated effort to understand the OT landscape's unique topography and distinctive security challenges.

Three security vulnerabilities have been disclosed in operational technology products from Wago and Schneider Electric. The flaws, per Forescout, are part of a broader set of shortcomings collectively called OT:ICEFALL, which now comprises a total of 61 issues spanning 13 different vendors.

The landscape of OT security tools is far less developed than its information technology counterpart. With OT systems opening to the world and cyberthreats surging, the lack of OT-specific security tools has emerged as an urgent problem.

"Fortinet's report shows that while OT organizations have improved their overall cybersecurity posture, they also have continued opportunity for improvement. Networking and IT teams are under extraordinary pressure to adapt and become more OT-aware, and organizations are shifting to find and employ solutions that implement security across their entire IT/OT environment to reduce their overall security risk," said John Maddison, EVP Products and CMO at Fortinet. While the number of organizations that did not incur a cybersecurity intrusion improved dramatically YoY, there is still significant room for improvement.

In response to these risks, the US government reinforced critical infrastructure security by introducing Cross-Sector Cybersecurity Performance Goals mandated by the US Cybersecurity Infrastructure & Security Agency. Recently, CISA updated the CPGs to align with NIST's standard cybersecurity framework, establishing each of the five goals as a prioritized subset of IT and OT cybersecurity practices.

In the fast-evolving landscape of technology and connectivity, ensuring the security of operational technology systems has become a paramount concern for organizations worldwide. In this Help Net Security video, Daniel Bren, CEO at OTORIO, discusses a significant discrepancy between how companies perceive their OT security posture and the harsh reality they often face.
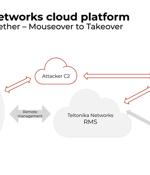
Several security vulnerabilities have been disclosed in cloud management platforms associated with three industrial cellular router vendors that could expose operational technology networks to external attacks. The 11 vulnerabilities allow "Remote code execution and full control over hundreds of thousands of devices and OT networks - in some cases, even those not actively configured to use the cloud."

The underlying trend is clear: OT and IoT networks are progressively integrated with traditional IT networks for management and access purposes, leading to increased communication between these devices both internally and externally. Controlling and overseeing supplier access to OT and IoT networks is challenging, as connections between external and internal networks can occur through various means like VPNs, direct mobile connections, and jump hosts.

CryPLH is a low-interactive and virtual Smart-Grid ICS honeypot simulating Siemens Simatic 300 PLC devices. With the development of cybersecurity technology, deception has been applied in various circumstances like the web, databases, mobile apps, and IoT. Deception technology has been embodied in some ICS honeypot applications in the OT field.