Security News

CISA has released RedEye, an interactive open-source analytic tool to visualize and report Red Team command and control activities. RedEye, available on GitHub, allows an operator to assess and display complex data, evaluate mitigation strategies, and enable effective decision-making in response to a Red Team assessment.

Open-source software is a critical element of the software supply chain in companies of all sizes, but there are new security concerns for the open-source software supply chain - calling for better approaches to packaging security, according to VMware. Top-level findings from The State of the Software Supply Chain: Open Source Edition 2022, show that OSS is clearly fulfilling stakeholder expectations for cost efficiency, increased flexibility, and developer productivity.

The U.S. Cybersecurity and Infrastructure Security agency has announced RedEye, an open-source analytic tool for operators to visualize and report command and control activity. A joint project from CISA and DOE's Pacific Northwest National Laboratory, RedEye can parse logs from attack frameworks to present complex data in a more digestible format.

Confidential Computing is a hardware-based technology that shields computer workloads from their environments and keeps data encrypted during processing. In this Help Net Security video, Felix Schuster, CEO at Edgeless Systems, talks about the open-source release of Constellation.
A game changer in cyber incident response, the Dissect framework enables data acquisition on thousands of systems within hours, regardless of the nature and size of the IT environment to be investigated after an attack. Now it is available on GitHub to the security community as open source software to help advance and accelerate forensic data collection and analysis.

The pros and cons of OSS. The challenge of OSS security is that just because everyone can look at the source code, it does not mean anyone will. A recent report from the Linux Foundation found that the average number of outstanding critical vulnerabilities in an application is 5.1, and that 41% of organizations are not confident in their open source software security.
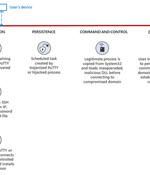
A "Highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022. Attacks targeted employees in organizations across multiple industries, including media, defense and aerospace, and IT services in the U.S., the U.K., India, and Russia.

Microsoft says the North Korean-sponsored Lazarus threat group is trojanizing legitimate open-source software and using it to backdoor organizations in many industry sectors, such as technology, defense, and media entertainment. The list of open-source software weaponized by Lazarus state hackers to deploy the BLINDINGCAN backdoor includes PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and the muPDF/Subliminal Recording software installer.

Wazuh is a free and open source security platform that provides unified SIEM and XDR protection. Wazuh central components that analyze security data collected from the agents.

Wazuh is an open source unified XDR and SIEM platform. The Wazuh agent collects security event data from the monitored endpoints and forwards them to the Wazuh server for log analysis, correlation, and alerting.