Security News

A former IT consultant hacked a company in Carlsbad, California, and deleted almost all its Microsoft Office 365 accounts in an act of revenge that has brought him two years of prison time. More than 1,200 user accounts were removed in this act of sabotage, causing a complete shutdown of the company's operations for two days.

A former IT contractor has been sentenced to two years in prison after hacking into a company's server and deleting the majority of its employees' Microsoft Office 365 accounts. On Aug. 8, 2018, Kher then hacked into the company's server and deleted over 1,200 of its 1,500 O365 user accounts.

A California federal court has sentenced a "Vengeful" techie to two years in the clink after he deleted 1,200 Microsoft user accounts belonging to a client. Deepanshu Kher, a Delhi-based employee of an unnamed IT outsourcing firm, was tasked with helping a company in the coastal city of Carlsbad, California, migrate its Office 365 environment.

A new phishing scam is on the rise, targeting executives in the insurance and financial services industries to harvest their Microsoft 365 credentials and launch business email compromise attacks, according to a new report from Area 1 Security. These new, sophisticated attacks are aimed at C-suite executives, their assistants and financial departments, and can work around email security and Office 365 defenses.

A sophisticated and highly targeted Microsoft Office 365 phishing campaign is being aimed at C-suite executives, executive assistants and financial departments across numerous industries. The threat actors are leveraging phishing kits and a number of sophisticated methods at every step of the attack.

A quick shift toward Microsoft Office 365 and Azure AD in the cloud has expanded the attack surface for many organizations, says Vectra AI. The coronavirus pandemic has forced many organizations to transition their applications and other assets to the cloud. This increased reliance on Office 365 has naturally caught the eye of cybercriminals who have been ramping up their attacks against Microsoft's cloud-based Office environment for many customers.
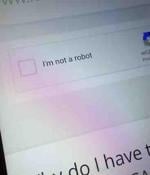
Microsoft users are being targeted with thousands of phishing emails, in an ongoing attack aiming to steal their Office 365 credentials. The attackers add an air of legitimacy to the campaign by leveraging a fake Google reCAPTCHA system and top-level domain landing pages that include the logos of victims' companies.

Microsoft has added XLM macro protection for Microsoft 365 customers by expanding the runtime defense provided by Office 365's integration with Antimalware Scan Interface to include Excel 4.0 macro scanning. Microsoft first extended support for its Antimalware Scan Interface to Office 365 client applications in 2018 to defend customers against attacks using VBA macros.

Designed as cloud-native software, BitDam ATP+ is the only solution that protects Office 365 users from unknown threats at first sight. Office 365 ATP, which is considered to have high detections rates, misses more than 25% of the unknown content-borne threats each day.

Microsoft is adding new security warnings to the Security and Compliance Center default alert policies to inform IT admins of detected phishing attempts abusing Microsoft Forms in their tenants. It has recently been made available for personal use to anyone with a Microsoft account after previously being available only to business users with Microsoft 365 Personal and Microsoft 365 Family subscriptions.