Security News

The Maui ransomware that has been used against US healthcare operations has been linked to Andariel, a North Korean state-sponsored threat with links to the notorious Lazarus Group. Ariel has been active since 2015, running attacks to steal data and bring in revenue for the North Korean regime.

The Maui ransomware operation has been linked to the North Korean state-sponsored hacking group 'Andariel,' known for using malicious cyber activities to generate revenue and causing discord in South Korea. State-sponsored North Korean hackers are notorious for orchestrating campaigns with financial motives, so running their own ransomware operation matches their overall strategic goals.

The U.S. Treasury Department's Office of Foreign Assets Control sanctioned Tornado Cash today, a decentralized cryptocurrency mixer service used to launder more than $7 billion since its creation in 2019. The North Korean-backed APT Lazarus Group also used the crypto mixer to launder approximately $455 million stolen in the largest known cryptocurrency heist ever.

A new social engineering campaign by the notorious North Korean Lazarus hacking group has been discovered, with the hackers impersonating Coinbase to target employees in the fintech industry. A common tactic the hacking group uses is to approach targets over LinkedIn to present a job offer and hold a preliminary discussion as part of a social engineering attack.
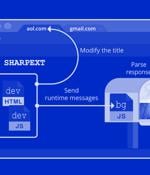
A threat actor operating with interests aligned with North Korea has been deploying a malicious extension on Chromium-based web browsers that's capable of stealing email content from Gmail and AOL. Cybersecurity firm Volexity attributed the malware to an activity cluster it calls SharpTongue, which is said to share overlaps with an adversarial collective publicly referred to under the name Kimsuky. SharpTongue has a history of singling out individuals working for organizations in the U.S., Europe, and South Korea who "Work on topics involving North Korea, nuclear issues, weapons systems, and other matters of strategic interest to North Korea," researchers Paul Rascagneres and Thomas Lancaster said.

The U.S. State Department has announced rewards of up to $10 million for any information that could help disrupt North Korea's cryptocurrency theft, cyber-espionage, and other illicit state-backed activities. "If you have information on any individuals associated with the North Korean government-linked malicious cyber groups and who are involved in targeting U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act, you may be eligible for a reward," the department said in a tweet.

The US is offering up to $10 million for information on members of state-sponsored North Korean threat groups, double the amount that the State Department announced in April. The agency's Rewards for Justice program this week said it will cough up the cash for intelligence related to "Government-linked cyber activities" in North Korea, including leads on people involved with such state-sponsored groups like Andariel, APT38, BlueNoroff, Guardians of Peace, Kimsuky, and Lazarus Group who are targeting critical infrastructure in the US. The latest notice is part of a larger ongoing campaign by the State Department and other US government agencies of offering bounties for information regarding cyberattacks from North Korea or other countries against the United States, particularly involving such sectors as critical infrastructure - such as power grids and water and food supplies - as well as federal elections.

"If you have information on any individuals associated with the North Korean government-linked malicious cyber groups and who are involved in targeting U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act, you may be eligible for a reward," the Department revealed Tuesday. One month later, the FBI linked the largest crypto hack ever to two North Korean hacking groups, Lazarus and BlueNorOff, saying they were responsible for the theft of $620 million in Ethereum from Axie Infinity's Ronin network bridge.

The U.S. State Department has increased rewards paid to anyone providing information on any North Korean-sponsored threat groups' members to $10 million. These increased bounties add to rewards of up to $5 million announced by the State Department in March for info on DPRK-backed threat actors targeting crypto exchanges and financial institutions worldwide to support the North Korean regime's illicit activities.

The U.S. Department of Justice has announced the seizure of $500,000 worth of Bitcoin from North Korean hackers who extorted digital payments from several organizations by using a new ransomware strain known as Maui. The DoJ did not disclose where the rest of the payments originated from.