Security News

The 2024 MITRE ATT&CK Evaluation results are now available with Cynet achieving 100% Visibility and 100% Protection in the 2024 evaluation. Learn more from Cynet about what these results mean. [...]

In today’s dynamic threat landscape, security leaders are under constant pressure to make informed choices about which solutions and strategies they employ to protect their organizations. The...

The "MITRE Engenuity ATT&CK Evaluations: Enterprise" stand out as an essential resource for cybersecurity decision makers. Learn more from Cynet on what to expect in the upcoming 2024 MITRE ATT&CK...

MITRE has shared this year's top 25 list of the most common and dangerous software weaknesses behind more than 31,000 vulnerabilities disclosed between June 2023 and June 2024. [...]

The MITRE Corporation has revealed that the cyber attack targeting the not-for-profit company towards late December 2023 by exploiting zero-day flaws in Ivanti Connect Secure (ICS) involved the...
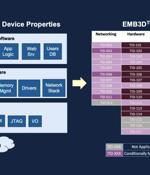
The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments. "The model provides a...

MITRE has shared a timeline of the recent breach if fell victim to and has confirmed that it began earlier than previously thought: on December 31, 2023. Tools and techniques used to breach MITRE. The attackers leveraged the Ivanti zero-days to gain access to the organization's research and prototyping network, from which they performed additional reconnaissance, moved into its VMware environment and exfitrated data.

The MITRE Corporation has offered more details into the recently disclosed cyber attack, stating that the first evidence of the intrusion now dates back to December 31, 2023. The attack,...

Hackers backdoored Cisco ASA devices via two zero-daysA state-sponsored threat actor has managed to compromise Cisco Adaptive Security Appliances used on government networks across the globe and use two zero-day vulnerabilities to install backdoors on them, Cisco Talos researchers have shared on Wednesday. How to optimize your bug bounty programsIn this Help Net Security interview, Roy Davis, Manager - Vulnerability Management & Bug Bounty at Zoom, discusses the role bug bounty programs play in identifying security vulnerabilities and facilitating collaboration with researchers.

MITRE has been breached by attackers via two zero-day vulnerabilities in Ivanti's Connect Secure VPN devices. The attackers have also managed to move laterally and compromise the company network's VMware infrastructure, MITRE confirmed late last week.