Security News

Attack surface expansion is a byproduct of doing business today, especially for enterprises that rely on the cloud. This can result in attack surface exposures, both known and unknown, giving malicious actors many pathways to gain entry to networks.

Syxsense now offers more IT and endpoint management functions, including mobile device management, automation, remediation and zero trust. Syxsense recently unveiled its all-encompassing suite - Syxsense Enterprise, which comes with patch and vulnerability management, MDM, zero trust, automation and orchestration capabilities, and remediation.

Given attack surface sprawl and evolving threats, many organizations are embracing attack surface management tools to discover and address critical exposures. Asset discovery is an important capability to have, and one that's helping to drive the adoption of attack surface management tools and services.

Learn how NetSPI's always-on solution allows companies to improve visibility, inventory, and understanding of known and unknown assets and exposures on their global attack surface and distill signal from noise. The discovery of assets and vulnerabilities is table stakes.

As it evolves into a critical component of threat and exposure management strategies, it's worth examining why attack surface management has grown to become a key category, and why it will continue to be a necessity for organizations worldwide. The attack surface includes any IT asset connected to the internet - applications, IoT devices, Kubernetes clusters, cloud platforms - that threat actors could infiltrate and exploit to perpetuate an attack.

Our desire for innovation, speed and efficiency has birthed new and complex security challenges that all in some way or another revolve around securing how we access resources. Because of this, effective access management now plays a more critical role in securing the modern workplace than ever.

Prism Infosec has identified two high-risk vulnerabilities within the Aspect Control Engine building management system developed by ABB. ABB's Aspect BMS enables users to monitor a building's performance and combines real-time integrated control, supervision, data logging, alarming, scheduling and network management functions with internet connectivity and web serving capabilities. During a recent security testing engagement on behalf of a client, researchers discovered an ABB Aspect appliance and that the BMS was misconfigured to be publicly available over the internet.
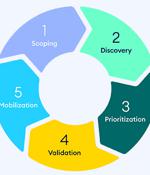
3 Challenges in Building a Continuous Threat Exposure Management (CTEM) Program and How to Beat Them
In this article, we'll look at another trending acronym - CTEM, which stands for Continuous Threat Exposure Management - and the often-surprising challenges that come along with seeing a CTEM program through to maturity. Continuous Threat Exposure Management is not a technology and you can't go to a vendor in hopes of finding a CTEM solution.

To have a successful conclusion to the mergers and acquisitions process, identity and access management teams need time to prepare, test, and communicate with users to ensure the process goes as smoothly as possible. Unauthorized access: During a rapid transition, there is often temporary confusion regarding who has access to sensitive data.

In this Help Net Security video interview, Or Weis, Co-Founder and CEO of Permit.io, discusses an innovative approach to managing permissions and access control within applications. We will explore policy as code and how it addresses organizations' challenges in managing access control effectively.