Security News
Meta said it took steps to take down more than 1,000 malicious URLs from being shared across its services that were found to leverage OpenAI's ChatGPT as a lure to propagate about 10 malware families since March 2023. The development comes against the backdrop of fake ChatGPT web browser extensions being increasingly used to steal users' Facebook account credentials with an aim to run unauthorized ads from hijacked business accounts.

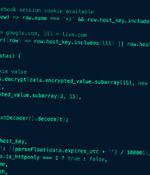
Facebook discovered a new information-stealing malware distributed on Meta called 'NodeStealer,' allowing threat actors to steal browser cookies to hijack accounts on the platform, as well as Gmail and Outlook accounts. As Facebook's security team explains in a new blog post, it identified NodeStealer early in its distribution campaign, only two weeks after its initial deployment.
Trend Micro attributed the intrusion set to a cyber espionage group it tracks under the name Earth Longzhi, which is a subgroup within APT41 and shares overlaps with various other clusters known as Earth Baku, SparklingGoblin, and GroupCC. Earth Longzhi was first documented by the cybersecurity firm in November 2022, detailing its attacks against various organizations located in East and Southeast Asia as well as Ukraine. Attack chains mounted by the threat actor leverage vulnerable public-facing applications as entry points to deploy the BEHINDER web shell, and then leverage that access to drop additional payloads, including a new variant of a Cobalt Strike loader called CroxLoader.
The North Korean threat actor known as ScarCruft began experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default. Other bespoke malware used by the group include, but not limited to, Chinotto, BLUELIGHT, GOLDBACKDOOR, Dolphin, and, most recently, M2RAT. It's also known to use commodity malware such as Amadey, a downloader that can receive commands from the attacker to download additional malware, in a bid to confuse attribution.

A new malware known as 'LOBSHOT' distributed using Google ads allows threat actors to stealthily take over infected Windows devices using hVNC. Earlier this year, BleepingComputer and numerous cybersecurity researchers reported a dramatic increase in threat actors utilizing Google ads to distribute malware in search results. In a new report by Elastic Security Labs, researchers revealed that a new remote access trojan named LOBSHOT was being distributed through Google Ads.
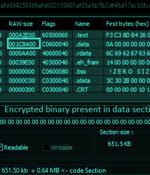
An analysis of over 70 billion DNS records has led to the discovery of a new sophisticated malware toolkit dubbed Decoy Dog targeting enterprise networks. "Decoy Dog is a cohesive toolkit with a number of highly unusual characteristics that make it uniquely identifiable, particularly when examining its domains on a DNS level," Infoblox said in an advisory published late last month.

The malware peddlers' focus on Apple fans was clearly reflected in the name they gave their "Product": Atomic macOS Stealer, or AMOS for short. Well-informed Mac users should spot that the popup produced clearly belongs to the malware app itself, which is imaginatively called Setup.

A new version of the ViperSoftX information-stealing malware has been discovered with a broader range of targets, including targeting the KeePass and 1Password password managers. The report comes from researchers at Trend Micro, who state that ViperSoftX now targets more cryptocurrency wallets than before, can infect different browsers besides Chrome, and is also starting to target password managers.

Threat actors are advertising a new information stealer for the Apple macOS operating system called Atomic macOS Stealer on Telegram for $1,000 per month, joining the likes of MacStealer. "The Atomic macOS Stealer can steal various types of information from the victim's machine, including Keychain passwords, complete system information, files from the desktop and documents folder, and even the macOS password," Cyble researchers said in a technical report.
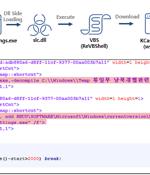
Construction, diplomatic, and political institutions are at the receiving end of new attacks perpetrated by a China-aligned threat actor known as the Tonto Team. "Recent cases have revealed that the group is using a file related to anti-malware products to ultimately execute their malicious attacks," the AhnLab Security Emergency Response Center said in a report published this week.