Security News

Hackers are distributing Windows 10 using torrents that hide cryptocurrency hijackers in the EFI partition to evade detection. The EFI partition is a small system partition containing the bootloader and related files executed before the operating system's startup.

He was the Gozi group's web expert, coding up bogus HTML content that the malware could inject into legitimate web pages in order to trick victims and steal their account information. Unlike many cybercriminals at the time, who profited from malware solely by using it to steal money, Kuzmin rented out Gozi to other criminals, pioneering the model of cybercriminals as service providers for other criminals.

The last of the three men said to be responsible for infecting Windows computers with the banking trojan Gozi has been sentenced to three years. Mihai Ionut Paunescu, 37, was said to have supplied the bulletproof hosting that is so vital for the efficient running of malware ops, allowing his co-conspirators to distribute the Gozi malware that stole confidential financial information from millions of computers, among them some Windows boxes running at NASA. The Romanian national, whom Feds say was also known as "Virus," was sentenced [PDF] to three years in prison on Monday.

Romanian national Mihai Ionut Paunescu, aka "Virus," was sentenced to three years in prison by a Manhattan federal court for running a bulletproof hosting service and facilitating the distribution of the Gozi, Zeus, SpyEye, and BlackEnergy malware. Bulletproof hosting services are web hosting companies in countries with lenient or non-enforced internet laws that follow relaxed policies regarding their clients' illicit content and activities.
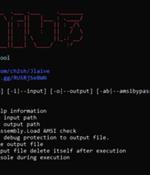
A fully undetectable malware obfuscation engine named BatCloak is being used to deploy various malware strains since September 2022, while persistently evading antivirus detection. The samples grant "Threat actors the ability to load numerous malware families and exploits with ease through highly obfuscated batch files," Trend Micro researchers said.

Mobile device backups contain a partial copy of the filesystem, including some of the user data and service databases. The timestamps of the files, folders and the database records allow to roughly reconstruct the events happening to the device.

Once they've broken into a victims' compute environment - often via compromised credentials - they keep quiet, deploying mining malware and then raking in cryptocurrencies using the stolen compute resources. Plus, according to security researchers, illicit mining is on the rise.

Hackers used the popular Minecraft modding platforms Bukkit and CurseForge to distribute a new 'Fractureiser' information-stealing malware through uploaded modifications and by injecting malicious code into existing projects. According to multiple reports, the attack began when several CurseForge and Bukkit accounts were compromised and used to inject malicious code into plugins and mods, which were then adopted by popular modpacks such as 'Better Minecraft,' which has over 4.6 million downloads.

An unknown threat actor has been observed targeting the U.S. aerospace industry with a new PowerShell-based malware called PowerDrop. "PowerDrop uses advanced techniques to evade detection such as deception, encoding, and encryption," according to Adlumin, which found the malware implanted in an unnamed domestic aerospace defense contractor in May 2023.

A recent malware campaign has been found to leverage Satacom downloader as a conduit to deploy stealthy malware capable of siphoning cryptocurrency using a rogue extension for Chromium-based browsers. "The main purpose of the malware that is dropped by the Satacom downloader is to steal BTC from the victim's account by performing web injections into targeted cryptocurrency websites," Kaspersky researchers Haim Zigel and Oleg Kupreev said.