Security News

South Korea issued a publicly available notice on Wednesday to wanted man and Terraform Labs founder Do Kwon, demanding he return his passport. The Ministry of Foreign Affairs disclosure [PDF] said that officials were unable to serve the notice to Kwon so had confirmed on its website that it was invalidating his passport and requesting its return within 14 days.

The infamous Lazarus Group has continued its pattern of leveraging unsolicited job opportunities to deploy malware targeting Apple's macOS operating system. In the latest variant of the campaign observed by cybersecurity company SentinelOne last week, decoy documents advertising positions for the Singapore-based cryptocurrency exchange firm Crypto.com.

South Korea's Personal Information Protection Commission has issued two large fines for privacy violations: a $50 million penalty for Google and $22 million for Meta. The PIPC's beef is that neither Google nor Meta properly obtain consent or inform users on how they collect and use data, particularly with regards to behavioral information used to predict interests for marketing and advertising purposes.

The North Korea-backed Lazarus Group has been observed targeting job seekers with malware capable of executing on Apple Macs with Intel and M1 chipsets. Slovak cybersecurity firm ESET linked it to a campaign dubbed "Operation In(ter)ception" that was first disclosed in June 2020 and involved using social engineering tactics to trick employees working in the aerospace and military sectors into opening decoy job offer documents.

Microsoft researchers have linked an emerging ransomware threat that already has compromised a number of small-to-mid-sized businesses to financially motivated North Korean state-sponsored actors that have been active since last year. A group tracked by researchers from Microsoft Threat Intelligence Center as DEV-0530 but that calls itself H0lyGh0st has been developing and using ransomware in attacks since June 2021.

US president Biden and South Korea's new president Yoon Suk Yeol have pledged further co-operation in many technologies, including joint efforts to combat North Korea. North Korea stands accused of running many offensive operations online.

The North Korea-backed Lazarus Group has been observed leveraging the Log4Shell vulnerability in VMware Horizon servers to deploy the NukeSped implant against targets located in its southern counterpart. NukeSped is a backdoor that can perform various malicious activities based on commands received from a remote attacker-controlled domain.
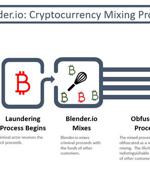
The U.S. Treasury Department on Friday moved to sanction virtual currency mixer Blender.io, marking the first time a mixing service has been subjected to economic blockades. Cryptocurrency mixers, also called tumblers, are privacy-focused services that allow users to move cryptocurrency assets between accounts without leaving a transaction trail by obfuscating their origins.

Cryptocurrency thief Lazarus Group appears to be widening its scope into using ransomware as a way to rip off financial institutions and other targets in the Asia-Pacific region, researchers have found. Financial transactions and similarities to previous malware in its source code link a recently emerged ransomware strain called VHD to the North Korean threat actors, also known as Unit 180 or APT35.

North Korea targeting blockchain, cryptocurrency companies. The advisory describes the recent activities of the Lazarus Group, who specialize in advanced persistent threats and target organizations in the blockchain and cryptocurrency industries.