Security News

Facebook last week began slapping "State controlled" labels on media outlets that it's determined are under the thumb of a government. According to NPR, as of Thursday's announcement, Pages and posts from at least 18 media outlets had been labelled "State-controlled media," including Russia Today, Russia's Sputnik News, China's People's Daily, China Xinhua News, and Iran's Press TV. The Facebook Pages for all of the outlets are now carrying transparency notices that advise users that they're "Wholly or partially under the editorial control of a state," as determined by factors including funding, structure and journalistic standards.

Today, cybersecurity researchers shed light on an Iranian cyber espionage campaign directed against critical infrastructures in Kuwait and Saudi Arabia. "Telecommunications firms are attractive targets given that they store large amounts of personal and customer information, provide access to critical infrastructure used for communications, and enable access to a wide range of potential targets across multiple verticals," the company said.

Today, cybersecurity researchers shed light on an Iranian cyber espionage campaign directed against critical infrastructures in Kuwait and Saudi Arabia. "Telecommunications firms are attractive targets given that they store large amounts of personal and customer information, provide access to critical infrastructure used for communications, and enable access to a wide range of potential targets across multiple verticals," the company said.

The Iranian cyber-espionage group referred to as MuddyWater continues to focus on long-running operations even after a U.S. airstrike killed General Qassem Soleimani on January 2. Cyber-retaliation continues to be a probability, and even industrial systems might be at risk, but for now Iranian threat groups appear to focus on their long-running cyber-espionage activity instead, Secureworks' security researchers say.

Researchers have attributed the campaign to a known Iranian advanced persistence threat group. As part of the campaign, researchers observed multiple emails using malicious attachments to gain initial access.
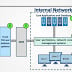
Exploiting VPN Flaws to Compromise Enterprise Networks The primary attack vector employed by the Iranian groups has been the exploitation of unpatched VPN vulnerabilities to penetrate and steal information from target companies. Once the attackers gained lateral movement capabilities, the attackers move to the final stage: execute the backdoor to scan the compromised system for relevant information and exfiltrate the files back to the attacker by establishing a remote desktop connection or opening a socket-based connection to a hardcoded IP address.

Now, security firm ClearSky says that at least three advanced persistent threat groups, all with apparent ties to the Iranian government, have been joining the fray and hitting unpatched Fortinet, Pulse Secure and Palo Alto Networks VPN servers and Citrix remote gateways. Specific flaws needing to be patched include CVE-2019-11510 in Pulse Secure's VPN SSL servers, CVE-2018-13379 in Fortigate's SSL VPN servers, and CVE-2019-1579 in Palo Alto Network VPN servers, all of which ClearSky says Fox Kitten is now exploiting.

Exploiting VPN Flaws to Compromise Enterprise Networks The primary attack vector employed by the Iranian groups has been the exploitation of unpatched VPN vulnerabilities to penetrate and steal information from target companies. Once the attackers gained lateral movement capabilities, the attackers move to the final stage: execute the backdoor to scan the compromised system for relevant information and exfiltrate the files back to the attacker by establishing a remote desktop connection or opening a socket-based connection to a hardcoded IP address.

Infamous Iranian hacking groups APT33 and APT34 appear to have been working together for the past three years to compromise dozens of organizations worldwide, and their attacks involved some of the enterprise VPN vulnerabilities disclosed last year, ClearSky reports. Since 2017, the two groups likely collaborated as part of an offensive campaign targeted at numerous companies and organizations from the IT, telecommunications, oil and gas, aviation, government, and security sectors around the world, ClearSky says in a new report.

The newly detailed phishing attack, Certfa Lab says, is related to previously observed activity targeting a U.S. presidential candidate, government officials, media targets, and prominent expatriate Iranians, where the hackers employed an updated spear phishing technique. As part of the campaign, the threat actor created a fake account impersonating New York Times journalist Farnaz Fassihi journalist), to send fake interview invitations to victims and trick them into accessing phishing websites.