Security News

FUD is spreading about a weirdly named personal network that a reverse engineer stumbled across and which he said "Permanently" wrecked his iPhone's Wi-Fi. TL;DR version: The twitching inflicted on his iPhone, which he demonstrated in the 4-second Tweet below, wasn't permanent. As replies to the initial post pointed out, an iPhone's Wi-Fi can be restored by resetting network settings.
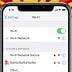
A wireless network naming bug has been discovered in Apple's iOS operating system that effectively disables an iPhone's ability to connect to a Wi-Fi network. The issue was spotted by security researcher Carl Schou, who found that the phone's Wi-Fi functionality gets permanently disabled after joining a Wi-Fi network with the unusual name "%p%s%s%s%s%n" even after rebooting the phone or changing the network's name.

A new iPhone bug has come to light that breaks your iPhone's wireless functionality by merely connecting to a specific WiFi hotspot. Once triggered, the bug would render your iPhone unable to establish a WiFi connection, even if it is rebooted or the WiFi hotspot is renamed.

A new iPhone bug has come to light that breaks your iPhone's wireless functionality by merely connecting to a specific WiFi hotspot. Once triggered, the bug would render your iPhone unable to establish a WiFi connection, even if it is rebooted or the WiFi hotspot is renamed.

The EU's proposed new rules to rein in tech giants risk undermining the security of the iPhone, Apple chief Tim Cook warned Wednesday. Cook, speaking at the VivaTech convention for startups in Paris, took aim at some of the rules that target online "Gatekeepers" such as Apple which controls which apps can be installed on its phones and tablets.

Microsoft has added support for detecting jailbroken iOS devices to Microsoft Defender for Endpoint, the enterprise version of its Windows 10 Defender antivirus. The new detection capability now available in the enterprise endpoint security platform will warn security teams of both managed and unmanaged jailbroken iPhones and iPads on their network.

Apple late Monday shipped an out-of-band iOS update for older iPhones and iPads alongside a warning that a pair of WebKit security vulnerabilities may have been actively exploited. As is customary, Apple did not provide details on the zero-day attacks, which appear to be aimed at a range of older models of Apple flagship iPhone devices.

In 2019, a Chinese security researcher working with the internet security and antivirus company Qihoo 360 unveiled an intricately woven exploit: One that would allegedly let a remote attacker easily jailbreak an iPhone X iOS 12.1. Allegedly shows, a successful exploit would allow a remote attacker to jailbreak an iPhoneX, with the targeted user none the wiser, allowing the intruder to gain access to a victim's data, processing power and more.

The new privacy feature, dubbed "App Tracking Transparency," rolled out Monday as part of an update to the operating system powering the iPhone and iPad. The anti-tracking shield included in iOS 14.5 arrives after a seven-month delay during which Apple and Facebook attacked each other's business models and motives for decisions that affect billions of people around the world. Apple takes a 15% to 30% cut on most payments processed through an iPhone app.

The Washington Post has published a long story on the unlocking of the San Bernardino Terrorist's iPhone 5C in 2016. We all thought it was an Israeli company called Cellebrite.