Security News

Numerous iOS apps are using background processes triggered by push notifications to collect user data about devices, potentially allowing the creation of fingerprinting profiles used for tracking. "Apps should not attempt to surreptitiously build a user profile based on collected data and may not attempt, facilitate, or encourage others to identify anonymous users or reconstruct user profiles based on data collected from Apple-provided APIs or any data that you say has been collected in an 'anonymized,' 'aggregated,' or otherwise non-identifiable way," reads a section of Apple App Store review guidelines.

Besides fixing an actively exploited zero-day vulnerability, the latest update for the iOS 17 branch offers a new feature to help you protect your accounts and sensitive information in case your iPhone gets stolen. If enabled, the Stolen Device Protection feature makes it difficult for iPhone thieves to switch certain features on or off and perform certain actions if your iPhone is not at a familiar location such as your home or work place.

Apple on Monday released security updates for iOS, iPadOS, macOS, tvOS, and Safari web browser to address a zero-day flaw that has come under active exploitation in the wild. The issue, tracked as...

Security researchers found that infections with high-profile spyware Pegasus, Reign, and Predator could be discovered on compromised Apple mobile devices by checking Shutdown. Kaspersky released Python scripts to help automate the process of analyzing the Shutdown.

Cybersecurity researchers have identified a "lightweight method" called iShutdown for reliably identifying signs of spyware on Apple iOS devices, including notorious threats like NSO...

See details Visit Atlas VPN. see details Visit Proton VPN. see details Visit PIA. For iPhone users, having a reliable virtual private network is crucial for maintaining security and privacy while using the internet. To help simplify the selection process, we have curated a list of the best VPNs for iPhone users.

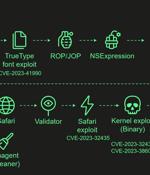
Kaspersky researchers are detailing "An attack that over four years backdoored dozens if not thousands of iPhones, many of which belonged to employees of Moscow-based security firm Kaspersky." It's a zero-click exploit that makes use of four iPhone zero-days. It uses return/jump oriented programming and multiple stages written in the NSExpression/NSPredicate query language, patching the JavaScriptCore library environment to execute a privilege escalation exploit written in JavaScript.

Kaspersky's Global Research and Analysis Team has exposed a previously unknown 'feature' in Apple iPhones that allows attackers to bypass hardware-based memory protection. Kaspersky reckons the hardware feature might have been intended for testing or debugging.
The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections...

The Operation Triangulation spyware attacks targeting iPhone devices since 2019 leveraged undocumented features in Apple chips to bypass hardware-based security protections. The discovery and use of obscure hardware features likely reserved for debugging and factory testing to launch spyware attacks against iPhone users suggest that a sophisticated threat actor conducted the campaign.