Security News

Two men have been convicted of hacking the taxi dispatch system at the JFK airport. This enabled them to reorder the taxis on the list; they charged taxi drivers $10 to cut the line.

While employees are preparing for some rest and relaxation, hackers are gearing up for their busy season. The holiday season is when hackers are the most active.
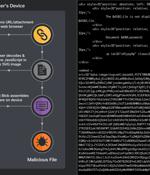
Phishing campaigns involving the Qakbot malware are using Scalable Vector Graphics images embedded in HTML email attachments. The new distribution method was spotted by Cisco Talos, which said it identified fraudulent email messages featuring HTML attachments with encoded SVG images that incorporate HTML script tags.

Interesting discussion of vulnerabilities and exploits against Boston’s CharlieCard.

This article talks about public land in the US that is completely surrounded by private land, which in some cases makes it inaccessible to the public. Ever since the Westward Expansion, much of the Western United States has been divided into alternating squares of public and private land.

Four men suspected of hacking into US networks to steal employee data for identity theft and the filing of fraudulent US tax returns have been arrested in London, UK, and Malmo, Sweden, at the request of the U.S. law enforcement authorities. The suspects identified in four recently unsealed U.S. indictments are Akinola Taylor, Olayemi Adafin, Olakunle Oyebanjo, and Kazeem Olanrewaju Runsewe.

The Department of Homeland Security Cyber Safety Review Board will review attacks linked to an extortion gang known as Lapsus$, which breached multiple high-profile companies in recent incidents. As announced on Friday, the goal behind CSRB's review of the gang's hacking activities is to provide advice on defending against Lapsus$ attacks.

Google Cloud last week disclosed that it identified 34 different hacked release versions of the Cobalt Strike tool in the wild, the earliest of which shipped in November 2012. The versions, spanning 1.44 to 4.7, add up to a total of 275 unique JAR files, according to findings from the Google Cloud Threat Intelligence team.

A previously unknown Chinese APT hacking group dubbed 'Earth Longzhi' targets organizations in East Asia, Southeast Asia, and Ukraine. The threat actors have been active since at least 2020, using custom versions of Cobalt Strike loaders to plant persistent backdoors on victims' systems.

Security researchers at Sentinel Labs have uncovered evidence that links the Black Basta ransomware gang to the financially motivated hacking group FIN7, also known as "Carbanak." When analyzing tools used by the ransomware gang in attacks, the researchers found signs that a developer for FIN7 has also authored the EDR evasion tools used exclusively by Black Basta since June 2022.