Security News

The attack started with compromising a media outlet's website to embed malicious scripts into an article, allowing for a 'watering hole' attack. State-backed North Korean hacking operations consistently rely on supply chain attacks and the exploitation of zero-day vulnerabilities as part of their cyber warfare tactics.

A North Korean state-sponsored threat actor tracked as Diamond Sleet is distributing a trojanized version of a legitimate application developed by a Taiwanese multimedia software developer called...

SiegedSec, which also claimed to have breached NATO's IT security on two occasions this year, said it has now hit Idaho National laboratory, which is run by the US Department of Energy's Office of Nuclear Energy. "On Monday, November 20, Idaho National Laboratory determined that it was the target of a cybersecurity data breach in a federally approved vendor system outside the lab that supports INL cloud Human Resources services," spokesperson Lori McNamara told The Register today.

Microsoft says a North Korean hacking group has breached Taiwanese multimedia software company CyberLink and trojanized one of its installers to push malware in a supply chain attack targeting potential victims worldwide. According to Microsoft Threat Intelligence, activity suspected to be linked with the altered CyberLink installer file surfaced as early as October 20, 2023.
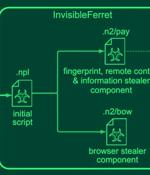
North Korean threat actors have been linked to two campaigns in which they masquerade as both job recruiters and seekers to distribute malware and obtain unauthorized employment with organizations...

Citrix reminded admins today that they must take additional measures after patching their NetScaler appliances against the CVE-2023-4966 'Citrix Bleed' vulnerability to secure vulnerable devices against attacks. Kill icaconnection -all kill rdp connection -all kill pcoipConnection -all kill aaa session -all clear lb persistentSessions.

The Kinsing threat actors are actively exploiting a critical security flaw in vulnerable Apache ActiveMQ servers to infect Linux systems with cryptocurrency miners and rootkits. "Once Kinsing...

The China-linked Mustang Panda actor has been linked to a cyber attack targeting a Philippines government entity amid rising tensions between the two countries over the disputed South China Sea....

Today’s security leaders must manage a constantly evolving attack surface and a dynamic threat environment due to interconnected devices, cloud services, IoT technologies, and hybrid work...

NDSC says that the Russian hackers used a Ngrok free static domain to access the command and control server hosted on their Ngrok instance. A report from Google in October notes that the security issue was exploited by Russian and Chinese state hackers to steal credentials and other sensitive data, as well as to establish persistence on target systems.