Security News

Security researchers have discovered 75 applications on Google Play and another ten on Apple's App Store engaged in ad fraud. The Satori team have informed Google and Apple about their findings and the apps have been removed from the official Android and iOS stores.

A new and upgraded version of the SharkBot malware has returned to Google's Play Store, targeting banking logins of Android users through apps that have tens of thousands of installations. Malware analysts at Cleafy, an Italian online fraud management and prevention company, discovered SharkBot in October 2021.

Google in November will prohibit Android VPN apps in its Play store from interfering with or blocking advertising, a change that may pose problems for some privacy applications. The T&Cs spell out that developers must declare the use of VPNservice in their apps' Google Play listing, must encrypt data from the device to the VPN endpoint, and must comply with Developer Program Policies, particularly those related to ad fraud, permissions, and malware.

A new batch of thirty-five malware Android apps that display unwanted advertisements was found on the Google Play Store, with the apps installed over 2 million times on victims' mobile devices. The apps were found by security researchers at Bitdefender, who employed a real-time behavior-based analysis method to discover the potentially malicious applications.

Several adware apps promoted aggressively on Facebook as system cleaners and optimizers for Android devices are counting millions of installations on Google Play store. To evade deletion, the apps hide on the victim's device by constantly changing icons and names, masquerading as Settings or the Play Store itself.
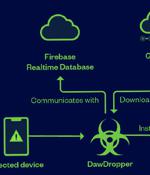
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware. These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others.

A new batch of malicious Android apps filled with adware and malware was found on the Google Play Store that have been installed close to 10 million times on mobile devices. If you installed any of these apps before their removal from the Play Store, you will still need to uninstall them from your device manually and run an AV scan to clean any remnants.

Cybersecurity researchers have discovered three Android malware families infiltrating the Google Play Store, hiding their malicious payloads inside many seemingly innocuous applications. The malicious activities suffered by users who installed the malware apps included stolen data, social media account takeovers, SMS interception, and unauthorized charges to their mobile numbers.

A new Android malware family on the Google Play Store that secretly subscribes users to premium services was downloaded over 3,000,000 times. The malware, named 'Autolycos,' was discovered by Evina's security researcher Maxime Ingrao to be in at least eight Android applications, two of which are still available on the Google Play Store at the time of this writing.

Cybersecurity researchers have discovered adware and information-stealing malware on the Google Play Store last month, with at least five still available and having amassed over two million downloads. Analysts at Dr. Web antivirus report that adware apps and data-stealing Trojans were among the most prominent Android threats in May 2022.