Security News

A large-scale fraud campaign leveraged fake trading apps published on the Apple App Store and Google Play Store, as well as phishing sites, to defraud victims, per findings from Group-IB. The...

A crypto draining app mimicking the legitimate 'WalletConnect' project has been distributed over Google Play for five months getting more than 10,000 downloads. [...]

A new version of the Necro Trojan malware for Android was installed on 11 million devices through Google Play in malicious SDK supply chain attacks. [...]

A new iteration of a sophisticated Android spyware called Mandrake has been discovered in five applications that were available for download from the Google Play Store and remained undetected for two years. A majority of the downloads originated from Canada, Germany, Italy, Mexico, Spain, Peru, and the U.K. "The new samples included new layers of obfuscation and evasion techniques, such as moving malicious functionality to obfuscated native libraries, using certificate pinning for C2 communications, and performing a wide array of tests to check if Mandrake was running on a rooted device or in an emulated environment," researchers Tatyana Shishkova and Igor Golovin said.

A new version of the Android spyware 'Mandrake' has been found in five applications downloaded 32,000 times from Google Play, the platform's official app store. Kaspersky now reports that a new variant of Mandrake that features better obfuscation and evasion sneaked into Google Play through five apps submitted to the store in 2022.
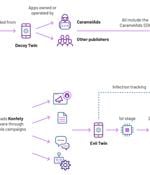
Details have emerged about a "Massive ad fraud operation" that leverages hundreds of apps on the Google Play Store to perform a host of nefarious activities. "Konfety represents a new form of fraud and obfuscation, in which threat actors operate 'evil twin' versions of 'decoy twin' apps available on major marketplaces," HUMAN's Satori Threat Intelligence Team said in a technical report shared with The Hacker News.

Over 90 malicious Android apps were found installed over 5.5 million times through Google Play to deliver malware and adware, with the Anatsa banking trojan seeing a recent surge in activity. In February 2024, Threat Fabric reported that since late last year, Anatsa had achieved at least 150,000 infections via Google Play using various decoy apps in the productivity software category.

Today, Google announced new security features coming to Android 15 and Google Play Protect that will help block scams, fraud, and malware apps on users' devices. "Today, we're announcing more new fraud and scam protection features coming in Android 15 and Google Play services updates later this year to help better protect users around the world," reads a Google blog post from Dave Kleidermacher, VP Engineering, Android Security and Privacy.

Today, Google announced new security features coming to Android 15 and Google Play that will help block scams, fraud, and malware apps on users' devices. "Today, we're announcing more new fraud and scam protection features coming in Android 15 and Google Play services updates later this year to help better protect users around the world," reads a Google blog post from Dave Kleidermacher, VP Engineering, Android Security and Privacy.

Over 15 free VPN apps on Google Play were found using a malicious software development kit that turned Android devices into unwitting residential proxies, likely used for cybercrime and shopping bots. HUMAN discovered the first PROXYLIB carrier app in May 2023, a free Android VPN app named "Oko VPN." The researchers later found the same library used by the LumiApps Android app monetization service.