Security News

A newly uncovered strain of Android spyware lurked on the Google Play Store disguised as cryptocurrency wallet Coinbase, among other things, for up to four years, according to a new report by Bitdefender. Beginning with an innocuous-looking dropper hosted on the Google Play store, masquerading as one of a number of legitimate apps, Mandrake allowed its Russian operators to snoop on virtually everything unsuspecting targets did on their mobile phone.
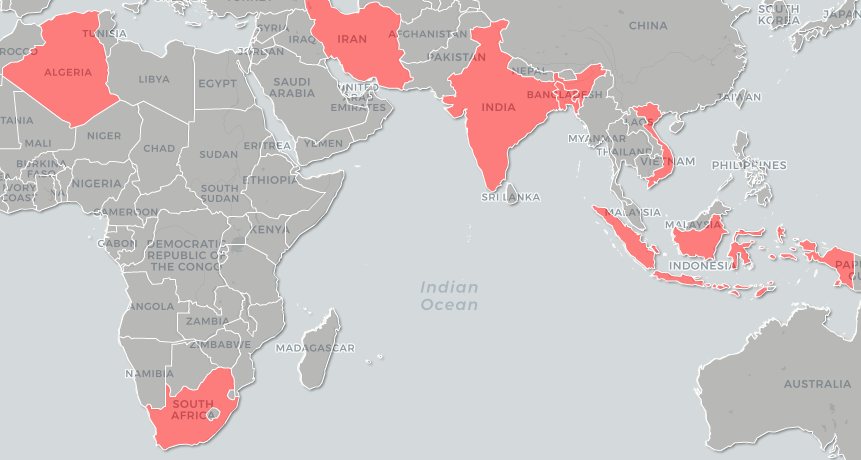
Dubbed PhantomLance by Kaspersky, the campaign is centered around a complex spyware that's distributed via dozens of apps within the Google Play official market, as well as other outlets like the third-party marketplace known as APKpure. Kaspersky's report follows previous research from BlackBerry, which connected OceanLotus to a trio of fake apps for Android last year.

Preying on public fears, the ongoing coronavirus outbreak is proving to be a goldmine of opportunity for attackers to stage a variety of malware attacks, phishing campaigns, and create scam sites and malicious tracker apps. Now in a fresh twist, third-party Android app developers too have begun to take advantage of the situation to use coronavirus-related keywords in their app names, descriptions, or in the package names so as to drop malware, perpetrate financial theft and rank higher in Google Play Store searches related to the topic.
More than 50 Android apps on the Google Play Store-most of which were designed for kids and had racked up almost 1 million downloads between them-have been caught using a new trick to secretly click on ads without the knowledge of smartphone users. While the offending apps have been removed from Google Play, the find by Check Point Research is the latest in an avalanche of ad fraud schemes that have plagued the app storefront in recent years, with malware posing as optimizer and utility apps to perform phony clicks on ads.
Researchers have discovered a new family of auto-clicker malware that commits mobile ad fraud, lurking in 56 apps on the Google Play store. Google's uphill battle against malware on Google Play is well known, and the vendor has made a concerted effort in the last couple of years to get rid of bad or unpatched apps and malware.

Researchers have identified eight malicious Android apps in the official Google Play marketplace distributing a new malware family. The comments under the Google Play download pages for these specific eight apps described the apps acting suspiciously, serving as red flags for potential downloaders.

Google Play Protect now scans over 100 billion applications on Android devices daily, according to new figures disclosed by Google this week. Google Play Protect is the protection mechanism built into the Android operating system to help protect devices and data from malware and other threats.

Malicious optimizer, booster, and utility applications hosted on Google Play gathered nearly half a million downloads before being taken down, Trend Micro reports. Four of the apps gathered more than 100,000 downloads each before Google removed them from the official storefront.

Google has made a concerted effort in recent months to try to eliminate bad apps for its Android mobile platform on the Google Play store-something the company historically has battled. These type of apps have been installed nearly 600 million times on 100 million plus devices, according to a Sophos report, which said it pulled the numbers from Google's own Google Play marketplace.

The treachery lies in the payment model - the fleeceware we identified back in September 2019 didn't charge a fee for the app, but instead sold you a subscription to go along with the app. The app's free, don't forget; it's the subscription that you're being charged for, and Google permits app developers to ask that sort of money.