Security News

Google has released Chrome 86.0.4240.111 today, October 20th, 2020, to the Stable desktop channel to address five security vulnerabilities, one of them an actively exploited zero-day bug. "Google is aware of reports that an exploit for CVE-2020-15999 exists in the wild," the Google Chrome 86.0.4240.111 announcement reads.
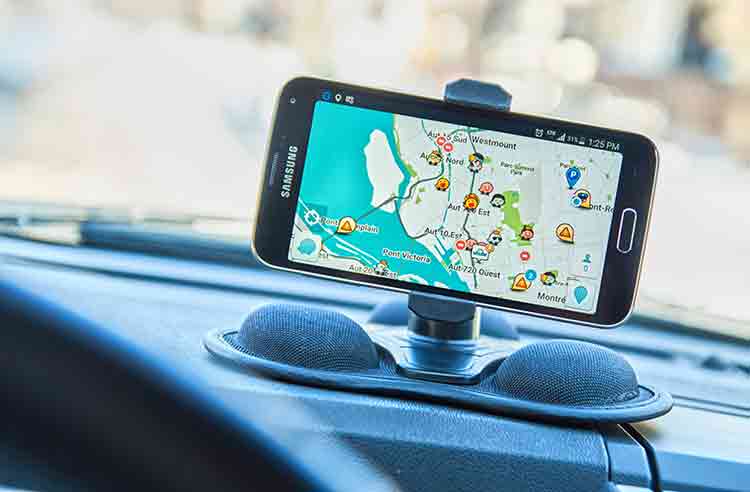
A security researcher has discovered a vulnerability in Google's Waze app that can allow hackers to identify people using the popular navigation app and track them by their location. Gasper reported the latest Waze bug to Google last December and was rewarded a bug bounty of $1,337 from Google's Vulnerability Reward Program in January 2020, disclosing the flaw publicly in August.

Google says its Threat Analysis Group hasn't observed any significant coordinated influence campaigns that are targeting United States voters on its platform. Google also notes that users who were identified as being targeted in such attacks were alerted, and that the Federal Bureau of Investigation was also informed of these attacks.

Google revealed last week that its infrastructure was targeted in a record-breaking distributed denial-of-service attack back in September 2017. In terms of bits per second, Google spotted the largest attack in September 2017.

A bug in the latest release of Chrome, and other Chromium-based browsers, is causing random debug. Log files to be created on user's desktops and other folders.

Google delivered over 33,000 alerts to its users during the first three quarters of 2020 to warn them of state-sponsored phishing attacks targeting their accounts. The prominent reminders sent to Google users targeted in government-backed attacks were displayed even when the hacking attempts were blocked to inform them of the danger.

The actor targeted thousands of Google IP addresses at the same time and used several attack methods in a campaign that span across multiple months. Google did not attribute the attack to a particular actor but said that the bad UDP packets hurled at its systems came from devices using several Chinese internet service providers.

Google security researchers are warning of a new set of zero-click vulnerabilities in the Linux Bluetooth software stack that can allow a nearby unauthenticated, remote attacker to execute arbitrary code with kernel privileges on vulnerable devices. According to security engineer Andy Nguyen, the three flaws - collectively called BleedingTooth - reside in the open-source BlueZ protocol stack that offers support for many of the core Bluetooth layers and protocols for Linux-based systems such as laptops and IoT devices.

Google and Intel are warning of a high-severity flaw in BlueZ, the Linux Bluetooth protocol stack that provides support for core Bluetooth layers and protocols to Linux-based internet of things devices. According to Google, the vulnerability affects users of Linux kernel versions before 5.9 that support BlueZ. BlueZ, which is an open-source project distributed under GNU General Public License, features the BlueZ kernel that has been part of the official Linux kernel since version 2.4.6.

The very nature of these searches requires mass surveillance. Homeland Security special agent Sylvette Reynoso testified that her team began by asking Google to produce a list of public IP addresses used to google the home of the victim in the run-up to the arson.