Security News

Mozilla this week pushed Firefox 90 to the stable channel with several security improvements, including better protections against cross-origin threats and an advanced tracker blocking mechanism. The open-source browser refresh is currently rolling out with support for Fetch Metadata Request Headers, which means that web applications can better protect users against cross-site request forgery, cross-site leaks, and speculative cross-site execution side channel attacks.

Mozilla has introduced SmartBlock 2.0, the next version of its intelligent cross-site tracking blocking tech, with the release of Firefox 90. The SmartBlock mechanism, introduced with Firefox 87 in March, works to ensure that the Tracking Protection feature and Strict Mode will not break websites when blocking tracking scripts.


Jack Wallen explains how to protect your web browsing from supercookies with Firefox's new privacy feature.

The Windows version of Firefox can now automatically upgrade itself to the latest version in the background when the web browser is not running. "Background Update is now available on Windows. This feature will allow Firefox to update, even if it is not running," the Firefox 90.0 Beta release notes read. "Until now, Firefox has only downloaded and installed updates when the user runs it. This means that users that use Firefox infrequently are often out-of-date," according to Kirk Steuber, Platform Engineer at Mozilla.

Mozilla says that Firefox users will be protected against cross-site tracking automatically while browsing the Internet in Private Browsing mode. This is because, starting with the Firefox 89 version released today, the Total Cookie Protection will be enabled by default in Private Browsing windows.

Mozilla advises Firefox users to update to the latest released version to avoid experiencing video streaming issues after Google updates the Widevine digital rights management on May 31. Once Google updates the Widevine private encryption keys and content decryption module on May 31, video streaming services using Google's DRM-protection technology will no longer work with older Firefox versions.

Firefox developers understand web browser security is at a premium, so they've started rolling out a new site isolation feature. That's a good thing because Firefox is an important browser that has brought about game-changing features over the years.
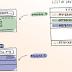
Mozilla has begun rolling out a new security feature for its Firefox browser in nightly and beta channels that aims to protect users against a new class of side-channel attacks from malicious sites. "This fundamental redesign of Firefox's Security architecture extends current security mechanisms by creating operating system process-level boundaries for all sites loaded in Firefox for Desktop," Mozilla said in a statement.

Mozilla has started rolling out the Site Isolation security feature to all Firefox channels, protecting users from attacks launched via malicious websites. Until today, Site Isolation could only be enabled by users of Firefox Nightly, the release channel used by Mozilla to test new features not yet ready for a wider rollout.