Security News
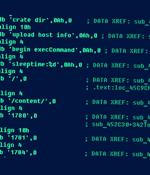
A nation-state actor with links to China is suspected of being behind a series of attacks against industrial organizations in Eastern Europe that took place last year to siphon data stored on air-gapped systems. The attacks entailed the use of more than 15 distinct implants and their variants, broken down into three broad categories based on their ability to establish persistent remote access, gather sensitive information, and transmit the collected data to actor-controlled infrastructure.
Instagram Threads, the upcoming Twitter competitor from Meta, will not be launched in the European Union due to privacy concerns, according to Ireland's Data Protection Commission. Threads is Meta's answer to Twitter that's set for launch on July 6, 2023.

Empowering Google security and networking solutions with AIIn this Help Net Security interview, Sunil Potti, GM and VP of Cloud Security at Google Cloud, talks about how new security and networking solutions powered by AI help improve security so Google customers can address their most pressing security challenges and remain ahead of an ever changing threat landscape. Infosecurity Europe 2023Infosecurity Europe took place at ExCeL London from June 20-22, 2023 and Help Net Security was on site.

Infosecurity Europe is taking place at ExCeL London from 20-22 June 2023 and Help Net Security is on site. The first gallery is available here, and the second gallery is here.

Infosecurity Europe 2023 is taking place in London this week, and this video provides a closer look at this year’s event. The post Infosecurity Europe 2023 video walkthrough appeared first on Help...

Infosecurity Europe 2023 is taking place at ExCeL London from 20-22 June 2023 and Help Net Security is on site. The first gallery is available here. Here’s a closer look at the conference...

Infosecurity Europe is taking place at ExCeL London from 20-22 June 2023 and Help Net Security is on site. Here’s a closer look at the conference featuring: Island, Crowdstrike, Panorays,...

European commissioner Thierry Breton wants Huawei and ZTE barred throughout the EU, and revealed plans to remove kit made by the Chinese telecom vendors from the Commission's internal networks. There are concerns that backdoors in Huawei equipment could allow China to spy on foreign nations, given Chinese law requires local businesses to share info with Beijing.

What if the enterprise had complete control over the browser? What would it do for security, productivity, for work itself? Ari Yablok, Head Of Brand at Island, invites you to visit Island at Infosecurity Europe 2023 to learn more.

In Germany alone, forced verification grew by 1500% as a proportion of all fraud cases, from 0.3% in the full year 2022 to 5% of all fraud in Q1 2023. In Great Britain and Europe, as well as in North America, the proportion of deepfakes among all fraud cases grew considerably from 2022 to Q1 2023.