Security News

Ransomware isn’t slowing down—it’s getting smarter. Encryption, designed to keep our online lives secure, is now being weaponized by cybercriminals to hide malware, steal data, and avoid...

Today, CISA urged senior government and political officials to switch to end-to-end encrypted messaging apps like Signal following a wave of telecom breaches across dozens of countries, including...

Cybersecurity researchers have identified a vulnerability (CVE-2024-21944, aka BadRAM) affecting ADM processors that can be triggered by rogue memory modules to unlock the chips’ encrypted memory....

Sounds like th-aorta get this sorted quickly A manufacturer of devices used in heart surgeries says it's dealing with "a cybersecurity incident" that bears all the hallmarks of a ransomware attack.…

FBI and Cybersecurity and Infrastructure Security Agency (CISA) officials have advised Americans to use encrypted call and messaging apps to protect their communications from threat actors that...

An international law enforcement operation codenamed 'Operation Passionflower' has shut down MATRIX, an encrypted messaging platform used by cybercriminals to coordinate illegal activities while...
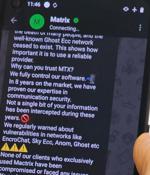
A joint investigation team involving French and Dutch authorities has taken down Matrix, yet another end-to-end encrypted chat service created for criminals. Matrix (Source: Dutch Police) The...

Apple has added a new security feature with the iOS 18.1 update released last month to ensure that iPhones automatically reboot after long idle periods to re-encrypt data and make it harder to...

MongoDB Queryable Encryption allows customers to securely encrypt sensitive application data and store it in an encrypted format within the MongoDB database. It also enables direct equality and...

Europol and law enforcement from nine countries successfully dismantled an encrypted communications platform called "Ghost," which was used by organized crime such as drug trafficking and money...