Security News

This approach is all about data and resilience, not deliberately sabotaging your own network, according to two cybersecurity experts.

In this role, Ms. Beckham will oversee all financial operations while working closely with our leadership team to support Cyber Defense Labs' business strategy and anticipated growth. Ms. Beckham brings a proven track record of success in leading all aspects of corporate finance with strong expertise in financial management, budgeting and forecasting, risk mitigation, cost controls and strategic planning.
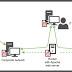
A prolific North Korean state-sponsored hacking group has been tied to a new ongoing espionage campaign aimed at exfiltrating sensitive information from organizations in the defense industry. The next-stage malware functions by embedding its malicious capabilities inside a Windows backdoor that offers features for initial reconnaissance and deploying malware for lateral movement and data exfiltration.

The prolific North Korean APT known as Lazarus is behind a spear-phishing campaign aimed at stealing critical data from defense companies by leveraging an advanced malware called ThreatNeedle, new research has revealed. The elaborate and ongoing cyberespionage campaign used emails with COVID-19 themes paired with publicly available personal information of targets to lure them into taking the malware bait, according to Kaspersky, which first observed the activity in mid-2020.

In early November, a developer contributing to Google's open-source Chromium project reported a problem with Oilpan, the garbage collector for the browser's Blink rendering engine: it can be used to break a memory defense known as address space layout randomization. About two weeks later, Google software security engineer Chris Palmer marked the bug "WontFix" because Google has resigned itself to the fact that ASLR can't be saved - Spectre and Spectre-like processor-level flaws can defeat it anyway, whether or not Oilpan can be exploited.

Kaspersky security researchers have found evidence that the North Korean hacking collective known as Lazarus has added another target to its list of victims: The defense industry, and companies in more than a dozen countries have already been affected. As previously reported by TechRepublic, Lazarus started off 2021 by targeting security researchers with offers of collaborating on malware research, only to infect victims with malware that could cause the theft of sensitive security-related data.

A North Korean-backed hacking group has targeted the defense industry with custom backdoor malware dubbed ThreatNeedle since early 2020 with the end goal of collecting highly sensitive information. ThreatNeedle helped the Lazarus hackers to move laterally throughout the defense orgs' networks and harvest sensitive info that got exfiltrated to attacker-controlled servers using a custom tunneling tool via SSH tunnels to remote compromised South Korean servers.

As browser-makers move to defang third-party cookies, marketers are increasingly switching to alternative tracking techniques. In 2019, Firefox was equipped with Enhanced Tracking Protection by default, blocking known trackers, third-party tracking cookies and cryptomining scripts.

Boffins based in Belgium have found that a DNS-based technique for bypassing defenses against online tracking has become increasingly common and represents a growing threat to both privacy and security. In a research paper to be presented in July at the 21st Privacy Enhancing Technologies Symposium, KU Leuven-affiliated researchers Yana Dimova, Gunes Acar, Wouter Joosen, and Tom Van Goethem, and privacy consultant Lukasz Olejnik, delve into increasing adoption of CNAME-based tracking, which abuses DNS records to erase the distinction between first-party and third-party contexts.

Sequitur Labs announced new packages for the EmSPARK Security Suite that allows manufacturers to secure embedded designs for industrial, consumer, smart home and health care applications quickly and painlessly. The EmSPARK Security Suite Base package provides essential security defenses for IoT applications in a turnkey solution that is easy to install, integrate and manage.