Security News

The only workaround recommended by Fortinet is to disable the SSL VPN. Disabling webmode won't mitigate the vulnerability, it said. Firstly, Fortinet backtracked and said these weren't vulnerabilities at all, instead explaining that they were issued in error and were duplicates of the single vulnerability mentioned in the aforementioned October advisory - CVE-2023-34992.

A widely reported story that 3 million electric toothbrushes were hacked with malware to conduct distributed denial of service attacks is likely a hypothetical scenario instead of an actual attack. Last week, Swiss news site Aargauer Zeitung published a story stating that an employee of cybersecurity firm Fortinet said 3 million electric toothbrushes had been infected with Java malware to conduct DDoS attacks against a Swiss company.

A widely reported story that 3 million electric toothbrushes were hacked with malware to conduct distributed denial of service attacks is likely a hypothetical scenario instead of an actual attack. Last week, Swiss news site Aargauer Zeitung published a story stating that an employee of cybersecurity firm Fortinet said 3 million electric toothbrushes had been infected with Java malware to conduct DDoS attacks against a Swiss company.

The Computer Emergency Response Team of Ukraine (CERT-UA) has warned that more than 2,000 computers in the country have been infected by a strain of malware called DirtyMoe. The...

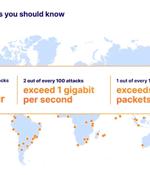
The maximum attack power rose from 800 Gbps to 1.6 Tbps. UDP floods continue to dominate, constituting 62% of DDoS attacks. In Q3/Q4, the longest attack duration lasted 9 hours, and the average length of attack was approximately an hour.

As we enter 2024, Gcore has released its latest Gcore Radar report, a twice-annual publication in which the company releases internal analytics to track DDoS attacks. Gcore’s broad,...
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half of all its HTTP traffic. This marks a 61,839%...

The impact of DDoS attacks extends far beyond mere inconvenience, as they can result in financial losses, compromised data, and erosion of customer trust. Understanding the nature and consequences of DDoS activity is essential for organizations and individuals alike as they strive to protect their online presence and ensure the uninterrupted flow of critical services.

A novel multi-platform threat called NKAbuse has been discovered using a decentralized, peer-to-peer network connectivity protocol known as NKN (short for New Kind of Network) as a communications...

The most recent Gcore Radar report and its aftermath have highlighted a dramatic increase in DDoS attacks across multiple industries. At the beginning of 2023, the average strength of...