Security News

Government entities in the Asia-Pacific (APAC) region are the target of a long-running cyber espionage campaign dubbed TetrisPhantom. "The attacker covertly spied on and harvested sensitive data...
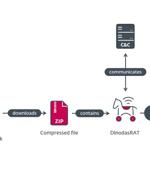
A governmental entity in Guyana has been targeted as part of a cyber espionage campaign dubbed Operation Jacana. The activity, which was detected by ESET in February 2023, entailed a...

China's Ministry of State Security (MSS) has accused the U.S. of breaking into Huawei's servers, stealing critical data, and implanting backdoors since 2009, amid mounting geopolitical tensions...

A Chinese espionage-focused hacker tracked as 'Earth Lusca' was observed targeting government agencies in multiple countries, using a new Linux backdoor dubbed 'SprySOCKS.'. Trend Micro's analysis of the novel backdoor showed that it originates from the Trochilus open-source Windows malware, with many of its functions ported to work on Linux systems.

A nation-state activity group originating from China has been linked to cyber attacks on dozens of organizations in Taiwan as part of a suspected espionage campaign. The Microsoft Threat Intelligence team is tracking the activity under the name Flax Typhoon, which is also known as Ethereal Panda.
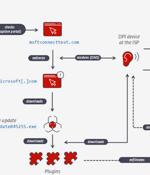
A hitherto undocumented threat actor operating for nearly a decade and codenamed MoustachedBouncer has been attributed to cyber espionage attacks aimed at foreign embassies in Belarus. "To compromise their targets, MoustachedBouncer operators tamper with their victims' internet access, probably at the ISP level, to make Windows believe it's behind a captive portal," Faou said.

The U.S. government on Tuesday added two foreign commercial spyware vendors, Cytrox and Intellexa, to an economic blocklist for weaponizing cyber exploits to gain unauthorized access to devices and "Threatening the privacy and security of individuals and organizations worldwide." Cytrox is the maker of a mobile mercenary spyware called Predator that's analogous to NSO Group's Pegasus.
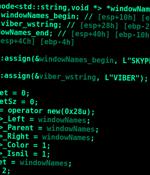
New findings about a hacker group linked to cyber attacks targeting companies in the Russo-Ukrainian conflict area reveal that it may have been around for much longer than previously thought. Bad Magic was first documented by the company in March 2023, detailing the group's use of a backdoor called PowerMagic and a modular framework dubbed CommonMagic in attacks targeting Russian-occupied territories of Ukraine.

The U.S. government on Tuesday announced the court-authorized disruption of a global network compromised by an advanced malware strain known as Snake wielded by Russia's Federal Security Service. Snake, dubbed the "Most sophisticated cyber espionage tool," is the handiwork of a Russian state-sponsored group called Turla, which the U.S. government attributes to a unit within Center 16 of the FSB. The threat actor has a track record of heavily focusing on entities in Europe, the Commonwealth of Independent States, and countries affiliated with NATO, with recent activity expanding its footprint to incorporate Middle Eastern nations deemed a threat to countries supported by Russia in the region.

Three different threat actors leveraged hundreds of elaborate fictitious personas on Facebook and Instagram to target individuals located in South Asia as part of disparate attacks. "Each of these APTs relied heavily on social engineering to trick people into clicking on malicious links, downloading malware or sharing personal information across the internet," Guy Rosen, chief information security officer at Meta, said.