Security News

Kinsing threat actors have been spotted exploiting the recently disclosed Looney Tunables vulnerability to covertly install cryptomining software into cloud-native environments. Kinsing is a threat actor group that has been active since late 2021, targeting cloud-native environments and applications - Kubernetes clusters, Docker API, Redis, Jenkins and Openfire servers, cloud-hosted Apache NiFi instances, and so on - to deploy cryptominers.
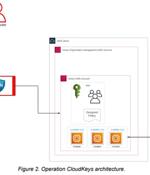
A new ongoing campaign dubbed EleKtra-Leak has set its eyes on exposed Amazon Web Service (AWS) identity and access management (IAM) credentials within public GitHub repositories to facilitate...
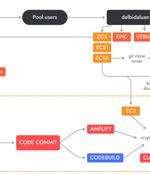
A novel cloud-native cryptojacking operation has set its eyes on uncommon Amazon Web Services offerings such as AWS Amplify, AWS Fargate, and Amazon SageMaker to illicitly mine cryptocurrency. "The AMBERSQUID operation was able to exploit cloud services without triggering the AWS requirement for approval of more resources, as would be the case if they only spammed EC2 instances," Sysdig security researcher Alessandro Brucato said in a report shared with The Hacker News.
A new, financially motivated operation dubbed LABRAT has been observed weaponizing a now-patched critical flaw in GitLab as part of a cryptojacking and proxyjacking campaign. Proxyjacking allows the attacker to rent the compromised host out to a proxy network, making it possible to monetize the unused bandwidth.

Digital threat actors are adopting evolving tactical behaviors, opting for different types of malicious attacks compared to previous years, according to SonicWall. Overall intrusion attempts were...

The Scarleteel threat targets AWS Fargate environments for data theft and more malicious types of attacks such as cryptojacking and DDoS. Learn how to mitigate this threat. Sysdig, a cloud and container security company, has released a new report on the Scarleteel threat that targets specific AWS environments for data theft and additional malicious activities.

Cloud environments continue to be at the receiving end of an ongoing advanced attack campaign dubbed SCARLETEEL, with the threat actors now setting their sights on Amazon Web Services Fargate. SCARLETEEL was first exposed by the cybersecurity company in February 2023, detailing a sophisticated attack chain that culminated in the theft of proprietary data from AWS infrastructure and the deployment of cryptocurrency miners to profit off the compromised systems' resources illegally.

Cybersecurity researchers have discovered previously undocumented payloads associated with a Romanian threat actor named Diicot, revealing its potential for launching distributed denial-of-service attacks. "The Diicot name is significant, as it's also the name of the Romanian organized crime and anti-terrorism policing unit," Cado Security said in a technical report.

New samples of the RapperBot botnet malware have added cryptojacking capabilites to mine for cryptocurrency on compromised Intel x64 machines. Researchers at Fortinet's FortiGuard Labs have been tracking RapperBot activity since June 2022 and reported that the Mirai-based botnet focused on brute-forcing Linux SSH servers to recruit them for launching distributed denial-of-service attacks.

With this cryptojacking attack, the threat actor scans for Kubernetes instances with the authentication parameter set as "-anonymous-auth=true". As stated by CrowdStrike researchers Benjamin Grap and Manoj Ahuje, "a user with sufficient privileges who runs 'kubectl proxy' can unintentionally expose a secure Kubernetes API on the host where kubectl is running, which is a less obvious way to expose the secure Kubernetes cluster bypassing authentication."