Security News

Researchers at Russian cybersecurity firm Kaspersky today revealed that they identified a small number of cryptocurrency-focused firms as at least some of the victims of the 3CX software supply-chain attack that's unfolded over the past week. Kaspersky declined to name any of those victim companies, but it notes that they're based in "Western Asia.".
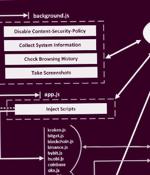
Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a seemingly legitimate extension to harvest sensitive data and siphon cryptocurrency. "Rilide malware is disguised as a legitimate Google Drive extension and enables threat actors to carry out a broad spectrum of malicious activities, including monitoring."

The Department of Justice declared the confiscation of digital currency valued at approximately $112 million connected to fraudulent cryptocurrency investments. In these schemes, fraudsters cultivate long-term relationships with victims met online, eventually enticing them to make investments in fraudulent cryptocurrency trading platforms.

The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number of cryptocurrency companies. The backdoor's links to North Korea stem from the fact that it "Co-existed on victim machines with AppleJeus, a backdoor attributed to the Korean-speaking threat actor Lazarus," detailing an attack on an unnamed crypto firm located in Southeast Asia in 2020.

Today, the U.S. Department of Justice seized six virtual currency accounts containing over $112 million in funds stolen in cryptocurrency investment schemes. The criminals behind these cryptocurrency fraud scams approach their victims via various dating platforms, messaging apps, or social media platforms, build trust, and introduce them to investment schemes which eventually allow them to empty the targets' crypto wallets.

Some of the victims affected by the 3CX supply chain attack have also had their systems backdoored with Gopuram malware, with the threat actors specifically targeting cryptocurrency companies with this additional malicious payload. VoIP communications company 3CX was compromised by North Korean threat actors tracked as Lazarus Group to infect the company's customers with trojanized versions of its Windows and macOS desktop apps in a large-scale supply chain attack. Kaspersky has discovered that the Gopuram backdoor previously used by the Lazarus hacking group against cryptocurrency companies since at least 2020, was also deployed as a second-stage payload in the same incident into the systems of a limited number of affected 3CX customers.

Copycat websites for instant messaging apps like Telegram and WhatApp are being used to distribute trojanized versions and infect Android and Windows users with cryptocurrency clipper malware. "All of them are after victims' cryptocurrency funds, with several targeting cryptocurrency wallets," ESET researchers Lukáš Štefanko and Peter Strý?ek said in a new analysis.

Cybercriminals are now using fake rewards in so-called "Play-to-earn" mobile and online games to steal millions worth of cryptocurrency, according to an FBI warning on Thursday. "Criminals contact victims online and build a relationship with victims over time," the FBI says in a public service announcement issued via the Internet Crime Complaint Center.

Nicholas Weaver wrote an excellent paper on the problems of cryptocurrencies and the need to regulate the space-with all existing regulations. The cryptocurrency space has grown over the past decade with very little regulatory oversight.

Cryptocurrency companies are being targeted as part of a new campaign that delivers a remote access trojan called Parallax RAT. The malware "Uses injection techniques to hide within legitimate processes, making it difficult to detect," Uptycs said in a new report. Parallax RAT grants attackers remote access to victim machines.