Security News

Multiple malware botnets actively target Cacti and Realtek vulnerabilities in campaigns detected between January and March 2023, spreading ShellBot and Moobot malware. The targeted flaws are CVE-2021-35394, a critical remote code execution vulnerability in Realtek Jungle SDK, and CVE-2022-46169, a critical command injection flaw in the Cacti fault management monitoring tool.

A new malware botnet was discovered targeting Realtek SDK, Huawei routers, and Hadoop YARN servers to recruit devices into DDoS swarm with the potential for massive attacks. Akamai's analysts created a C2 of their own and interacted with simulated infections to stage HinataBot for DDoS attacks to observe the malware in action and infer its attack capabilities.
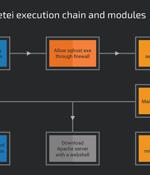
An updated version of a botnet malware called Prometei has infected more than 10,000 systems worldwide since November 2022. Prometei, first observed in 2016, is a modular botnet that features a large repertoire of components and several proliferation methods, some of which also include the exploitation of ProxyLogon Microsoft Exchange Server flaws.

A sophisticated botnet known as MyloBot has compromised thousands of systems, with most of them located in India, the U.S., Indonesia, and Iran. "What makes Mylobot dangerous is its ability to download and execute any type of payload after it infects a host," Lumen's Black Lotus Labs said in November 2018.

A new variant of the notorious Mirai botnet has been found leveraging several security vulnerabilities to propagate itself to Linux and IoT devices. "Once the vulnerable devices are compromised, they will be fully controlled by attackers and become a part of the botnet," Unit 42 researchers said.

A new Mirai botnet variant tracked as 'V3G4' targets 13 vulnerabilities in Linux-based servers and IoT devices to use in DDoS attacks. The malware spreads by brute-forcing weak or default telnet/SSH credentials and exploiting hardcoded flaws to perform remote code execution on the target devices.

A new version of the Medusa DDoS botnet, based on Mirai code, has appeared in the wild, featuring a ransomware module and a Telnet brute-forcer. Medusa is an old malware strain being advertised in darknet markets since 2015, which later added HTTP-based DDoS capabilities in 2017.

Hackers have leveraged a critical remote code execution vulnerability in Realtek Jungle SDK 134 million attacks trying to infect smart devices in the second half of 2022. Unit 42 logged activity leveraging CVE-2021-35394 from all over the world but almost half of the attacks originated from the United States.

The Zerobot DDoS botnet has received substantial updates that expand on its ability to target more internet-connected devices and scale its network. "The most recent distribution of Zerobot includes additional capabilities, such as exploiting vulnerabilities in Apache and Apache Spark, and new DDoS attack capabilities," Microsoft researchers said.
An ongoing analysis of the KmsdBot botnet has raised the possibility that it's a DDoS-for-hire service offered to other threat actors. KmsdBot is a Go-based malware that leverages SSH to infect systems and carry out activities like cryptocurrency mining and launch commands using TCP and UDP to mount distributed denial-of-service attacks.