Security News

Entities in the aviation, aerospace, transportation, manufacturing, and defense industries have been targeted by a persistent threat group since at least 2017 as part of a string of spear-phishing campaigns mounted to deliver a variety of remote access trojans on compromised systems. The use of commodity malware such as AsyncRAT and NetWire, among others, has led enterprise security firm Proofpoint to a "Cybercriminal threat actor" codenamed TA2541 that employs "Broad targeting with high volume messages." The ultimate objective of the intrusions is unknown as yet.

A previously undocumented threat actor has been identified as behind a string of attacks targeting fuel, energy, and aviation production industries in Russia, the U.S., India, Nepal, Taiwan, and Japan with the goal of stealing data from compromised networks. "The group compromised a subsidiary and penetrated the target company's network through it. Trusted relationship attacks are rare today due to the complexity of their execution. Using this method [], the ChamelGang group was able to achieve its goal and steal data from the compromised network."

Though attackers mainly have been seen targeting Russian organizations, they have attacked targets in 10 countries so far, researchers said in a report by company researchers Aleksandr Grigorian, Daniil Koloskov, Denis Kuvshinov and Stanislav Rakovsky published online Thursday. ChamelGang - like Nobelium and REvil before it - has hopped on the bandwagon of attacking the supply chain first to gain access to its ultimate target, they said.
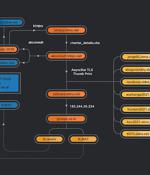
A targeted phishing campaign aimed at the aviation industry for two years may be spearheaded by a threat actor operating out of Nigeria, highlighting how attackers can carry out small-scale cyber offensives for extended periods of time while staying under the radar. Cisco Talos dubbed the malware attacks "Operation Layover," building on previous research from the Microsoft Security Intelligence team in May 2021 that delved into a "Dynamic campaign targeting the aerospace and travel sectors with spear-phishing emails that distribute an actively developed loader, which then delivers RevengeRAT or AsyncRAT.".

A phishing campaign that mostly targeted the global aviation industry may be connected to Nigeria, according to Cisco Talos. The malicious campaigns centred around phishing emails linking to "Off-the-shelf malware" being sent to people around the world - even those with a marginal interest in commercial aviation.

A cyberattack campaign that goes after aviation targets has been uncovered, which is spreading remote access trojan malware bent on cyber-espionage. Once installed, the RATs connect to a command-and-control server that's hosted on a dynamic hosting site to register with the attackers.

Microsoft warns of an ongoing spear-phishing campaign targeting aerospace and travel organizations with multiple remote access trojans deployed using a new and stealthy malware loader. "In the past few months, Microsoft has been tracking a dynamic campaign targeting the aerospace and travel sectors with spear-phishing emails that distribute an actively developed loader, which then delivers RevengeRAT or AsyncRAT," Microsoft said.

American aviation regulators have ordered private jet operators to install software updates for Garmin collision avoidance units after multiple reports of false alarms - raising the risk of a mid-air crash. The affected Garmin products, its GTS 8000 series, generated seven false Traffic Collision Avoidance System warnings, said the US Federal Aviation Administration in a formal Airworthiness Directive published [PDF] earlier this month.

Private aviation services provider Solairus Aviation on Tuesday announced that some employee and customer data was compromised in a security incident at third-party vendor Avianis. In a data breach announcement on March 23, Solairus said aviation business management platform provider Avianis provided notification last December about an intrusion into Avianis' Microsoft Azure cloud platform, which hosts Solairus flight scheduling and tracking system.

SITA, a multinational company that specializes in air transport communications and IT, this week confirmed falling victim to a cyberattack that appears to have impacted multiple airlines around the world. SITA said on Thursday that the attack, which it described as "Highly sophisticated," affected certain passenger data stored on servers of SITA Passenger Service System Inc., which operates passenger processing systems for airlines.