Security News

Cybersecurity researchers are alerting to a new malware campaign that employs the ClickFix social engineering tactic to trick users into downloading an information stealer malware known as Atomic...

Threat actors are continuing to upload malicious packages to the npm registry so as to tamper with already-installed local versions of legitimate libraries to execute malicious code in what's seen...

Cybersecurity researchers have identified an updated version of a macOS information stealer called Atomic (or AMOS), indicating that the threat actors behind the malware are actively enhancing its...

The 'ClearFake' fake browser update campaign has expanded to macOS, targeting Apple computers with Atomic Stealer malware. The ClearFake campaign started in July this year to target Windows users with fake Chrome update prompts that appear on breached sites via JavaScript injections.

Atomic Stealer Sends Macs Malware Through False Browser DownloadsTechRepublicToggle TechRepublic mobile menuTechRepublic PremiumTechRepublic close modalTechRepublic close modalTechRepublic close modalTechRepublicTechRepublic on TwitterTechRepublic on FacebookTechRepublic on LinkedInTechRepublic on FlipboardLoadingLoadingLoadingLoadingLoading. Anti-malware software provider Malwarebytes has described a new variant of Atomic Stealer, which is malware targeting Apple users.

The macOS information stealer known as Atomic is now being delivered to target via a bogus web browser update chain tracked as ClearFake. "This may very well be the first time we see one of the...
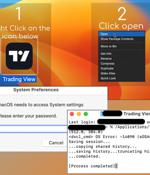
A new malvertising campaign has been observed distributing an updated version of a macOS stealer malware called Atomic Stealer, indicating that it's being actively maintained by its author. An off-the-shelf Golang malware available for $1,000 per month, Atomic Stealer first came to light in April 2023.

The North Korean criminal gang Lazarus Group has been blamed for last weekend's attack on Atomic Wallet that drained at least $35 million in cryptocurrency from private accounts. The researchers added that the "Stolen assets are being laundered using specific services, including the Sinbad mixer, which have also been used to launder the proceeds of past hacks perpetrated by the Lazarus Group." In addition, the stolen assets were mingled in wallets that also hold cryptocurrency stolen in previous attacks by the Lazarus Group.

The notorious North Korean hacking group known as Lazarus has been linked to the recent Atomic Wallet hack, resulting in the theft of over $35 million in crypto. The attack on Atomic Wallet occurred last weekend when numerous users reported that their wallets were compromised and their funds had been stolen.

The Atomic Wallet app's makers first reported June 3 that some folks were complaining some crypto had been taken from their wallets and deposited in strangers' accounts, with others saying their wallets had been emptied completely. The developer, headquartered in Tallinn, Estonia, says Atomic Wallet is a noncustodial app, meaning that users own the 12-word backup phrase and private keys to their coins, rather than the app maker, and that security is within the users' control.