Security News

Last week, Apple essentially invited security researchers to probe its forthcoming technology that's supposed to help thwart the spread of known child sexual abuse material. Crucially, Apple repeatedly stated that its claims about its CSAM-scanning software are "Subject to code inspection by security researchers like all other iOS device-side security claims." And its senior veep of software engineering Craig Federighi went on the record to say "Security researchers are constantly able to introspect what's happening in Apple's [phone] software."

Privacy groups like the Electronic Frontier Foundation warned that the process of flagging CSAM images essentially narrows the definition of end-to-end encryption to allow client-side access - which essentially means Apple is building a backdoor into its data storage, it said."Apple can explain at length how its technical implementation will preserve privacy and security in its proposed backdoor, but at the end of the day, even a thoroughly documented, carefully thought-out, and narrowly scoped backdoor is still a backdoor," The EFF said in reaction to the Apple announcement.

Too many of these - there's a threshold - and Apple's systems will let Apple staff investigate. In a blog post "Recognizing People in Photos Through Private On-Device Machine Learning" last month, Apple plumped itself up and strutted its funky stuff on how good its new person recognition process is.

A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone, some of which have slipped past Apple's on-device malware scanner and even signed by its own notarization service, highlighting the malicious software ongoing attempts to adapt and evade detection. The new iteration "Continues to impact Mac users who rely solely on Apple's built-in security control XProtect for malware detection," SentinelOne threat researcher Phil Stokes said in an analysis published last week.

A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone, some of which have slipped past Apple's on-device malware scanner and even signed by its own notarization service, highlighting the malicious software ongoing attempts to adapt and evade detection. The new iteration "Continues to impact Mac users who rely solely on Apple's built-in security control XProtect for malware detection," SentinelOne threat researcher Phil Stokes said in an analysis published last week.

Well, according to Apple, "Mail Privacy Protection stops senders from using invisible pixels to collect information about the user. senders from knowing when they open an email and masks their IP address so it can't be linked to other online activity or used to determine their location." Marketers' ability to deliver those experiences relies on these metrics and, due to Apple's Mail Privacy Protection, marketers will no longer be able to deliver those personalized and engaging email experiences for subscribers.

A swelling wave of AdLoad malware infections in macOS devices is cresting its way past Apple's on-device malware scanner, researchers said. AdLoad is a well-known Apple threat that's been circulating for years.

A new AdLoad malware variant is slipping through Apple's YARA signature-based XProtect built-in antivirus tech to infect Macs as part of multiple campaigns tracked by SentinelOne security researchers. While monitoring this campaign, the researchers observed more than 220 samples, 150 of them unique and undetected by Apple's built-in antivirus even though XProtect now comes with roughly a dozen AdLoad signatures.
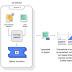
Apple on Thursday said it's introducing new child safety features in iOS, iPadOS, watchOS, and macOS as part of its efforts to limit the spread of Child Sexual Abuse Material in the U.S. To that effect, the iPhone maker said it intends to begin client-side scanning of images shared via every Apple device for known child abuse content as they are being uploaded into iCloud Photos, in addition to leveraging on-device machine learning to vet all iMessage images sent or received by minor accounts to warn parents of sexually explicit photos in the messaging platform. What's more, Apple is expected to use another cryptographic principle called threshold secret sharing that allows it to "Interpret" the contents if an iCloud Photos account crosses a threshold of known child abuse imagery, following which the content is manually reviewed to confirm there is a match, and if so, disable the user's account, report the material to NCMEC, and pass it on to law enforcement.

There are two main features that the company is planning to install in every Apple device. One is a scanning feature that will scan all photos as they get uploaded into iCloud Photos to see if they match a photo in the database of known child sexual abuse material maintained by the National Center for Missing & Exploited Children.