Security News

Microsoft has confirmed that Android apps are coming to Windows 11 and users will be able to try mobile apps on the desktop operating system soon, but the general availability has been delayed. Ahead of the beta testing with Insiders, Microsoft has already published the placeholder for the Android subsystem in the Microsoft Store.

A new Android banking trojan named SOVA is under active development, researchers said, and it has big dreams even in its infancy stage. "Regarding the development, SOVA also stands out for being fully developed in Kotlin, a coding language supported by Android and thought by many to be the future of Android development," according to ThreatFabric.
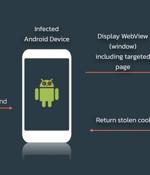
A mix of banking applications, cryptocurrency wallets, and shopping apps from the U.S. and Spain are the target of a newly discovered Android trojan that could enable attackers to siphon personally identifiable information from infected devices, including banking credentials and open the door for on-device fraud. Dubbed S.O.V.A., the current version of the banking malware comes with myriad features to steal credentials and session cookies through web overlay attacks, log keystrokes, hide notifications, and manipulate the clipboard to insert modified cryptocurrency wallet addresses, with future plans to incorporate on-device fraud through VNC, carry out DDoS attacks, deploy ransomware, and even intercept two-factor authentication codes.

Attackers have been targeting the Kurdish ethic group for more than a year through an Facebook-based spyware campaign that disguises backdoors in legitimate Android apps, researchers have found. The campaign disguises the 888 RAT in Android apps using dedicated Facebook profiles, researchers aid.

Figure A. Outside of the features Private Compute Core will bring to your device, one of the more important things it does is store data separate from all apps and services, while making that data available to the operating system when required. With Private Compute Core at work, that data is processed within its own sandbox, away from everything else, and then the captions are presented for your viewing.

Google says that users of some Android phone models are affected by a Google App bug preventing them from making and receiving calls. "After the latest update to the Google Search App on Android, the users of certain mobile phones are experiencing difficulty in receiving and making calls," a Google community manager said earlier today.

"The Trojan Triada snuck into one of these modified versions of the messenger called FMWhatsApp 16.80.0 together with the advertising software development kit," researchers from Russian cybersecurity firm Kaspersky said in a technical write-up published Tuesday. Modified versions of legitimate Android apps - a practice called Modding - are designed to perform functions not originally conceived or intended by the app developers.

"The Trojan Triada snuck into one of these modified versions of the messenger called FMWhatsApp 16.80.0 together with the advertising software development kit," researchers from Russian cybersecurity firm Kaspersky said in a technical write-up published Tuesday. Modified versions of legitimate Android apps - aka Modding - are designed to perform functions not originally conceived or intended by the app developers, and FMWhatsApp allows users to customize the app with different themes, personalize icons, and hide features like last seen, and even deactivate video calling features.

A malicious version of the FMWhatsappWhatsApp mod delivers a Triadatrojan payload, a nasty surprise that infects their devices with additional malware, including the very hard-to-remove xHelper trojan. FMWhatsApp promises to improve the WhatsApp user experience with added features such as better privacy, custom chat themes, access to other social networks' emoji packs, and app locking using a PIN, password, or the touch ID. However, as Kaspersky researchers found, the FMWhatsapp 16.80.0 version will also drop the Triada trojan on users' devices with the help of an advertising SDK. Trojan harvests device info and installs more malware.

UNISOC joins Google’s Android Ready SE Alliance to deliver secure solutions to the Android ecosystem
UNISOC announced that it has joined Google's new Android Ready SE Alliance, a collaboration between Google and Secure Element vendors, to offer a growing list of open-source, validated, and ready-to-use SE Applets for new and emerging use cases such as digital keys, identity credentials, E-money solutions. The alliance was created to make discrete tamper resistant hardware backed security the lowest common denominator for the Android ecosystem, which makes emerging applications on smart terminals more secure and convenient.