Security News

An unofficial version of the popular WhatsApp messaging app called YoWhatsApp has been observed deploying an Android trojan known as Triada. The goal of the malware is to steal the keys that "Allow the use of a WhatsApp account without the app," Kaspersky said in a new report.

A new version of an unofficial WhatsApp Android application named 'YoWhatsApp' has been found stealing access keys for users' accounts. YoWhatsApp is a fully working messenger app that uses the same permissions as the standard WhatsApp app and is promoted through advertisements on popular Android applications like Snaptube and Vidmate.

"We have now reached the point where SMS support no longer makes sense. In order to enable a more streamlined Signal experience, we are starting to phase out SMS support from the Android app," the company said in a blog post published today. Signal will start notifying them to export their SMS messages and switch to a new default app to manage their SMS messages.

Malicious actors are resorting to voice phishing tactics to dupe victims into installing Android malware on their devices, new research from ThreatFabric reveals. Telephone-oriented attack delivery, as the social engineering technique is called, involves calling the victims using previously collected information from fraudulent websites.
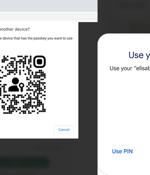
Google on Wednesday officially rolled out support for passkeys, the next-generation authentication standard, to both Android and Chrome. "Passkeys are a significantly safer replacement for passwords and other phishable authentication factors," the tech giant said.

Google announced today that it's introducing passkey support to its Chrome web browser and the Android operating system to simplify sign-ins across apps, websites, and devices. "Passkeys are a significantly safer replacement for passwords and other phishable authentication factors. They cannot be reused, don't leak in server breaches, and protect users from phishing attacks," Google said today.

Mullvad VPN has discovered that Android leaks traffic every time the device connects to a WiFi network, even if the "Block connections without VPN," or "Always-on VPN," features is enabled. The data being leaked outside VPN tunnels includes source IP addresses, DNS lookups, HTTPS traffic, and likely also NTP traffic.
Meta Platforms on Friday disclosed that it had identified over 400 malicious apps on Android and iOS that it said targeted online users with the goal of stealing their Facebook login information. 42.6% of the rogue apps were photo editors, followed by business utilities, phone utilities, games, VPNs, and lifestyle apps.

A novel Android malware called RatMilad has been observed targeting a Middle Eastern enterprise mobile device by concealing itself as a VPN and phone number spoofing app. The mobile trojan functions as advanced spyware with capabilities that receives and executes commands to collect and exfiltrate a wide variety of data from the infected mobile endpoint, Zimperium said in a report shared with The Hacker News.

A new Android spyware named 'RatMilad' was discovered targeting mobile devices in the Middle East, used to spy on victims and steal data. The RatMilad spyware was discovered by mobile security firm Zimperium who warned that the malware could be used for cyber espionage, extortion, or to eavesdrop on victim's conversations.