Security News > 2024 > December > Cleo File Transfer Vulnerability Under Exploitation – Patch Pending, Mitigation Urged
2024-12-10 15:57
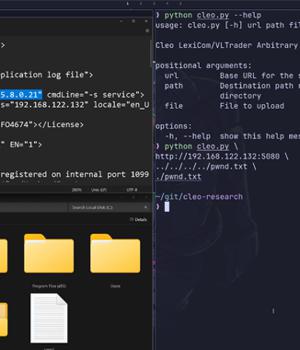
Users of Cleo-managed file transfer software are being urged to ensure that their instances are not exposed to the internet following reports of mass exploitation of a vulnerability affecting fully patched systems. Cybersecurity company Huntress said it discovered evidence of threat actors exploiting the issue en masse on December 3, 2024. The vulnerability, which impacts Cleo's LexiCom,
News URL
https://thehackernews.com/2024/12/cleo-file-transfer-vulnerability-under.html
Related news
- CrushFTP: Patch critical vulnerability ASAP! (CVE-2025-2825) (source)
- CISA Adds CrushFTP Vulnerability to KEV Catalog Following Confirmed Active Exploitation (source)
- OttoKit WordPress Plugin Admin Creation Vulnerability Under Active Exploitation (source)
- Gladinet’s Triofox and CentreStack Under Active Exploitation via Critical RCE Vulnerability (source)