Security News > 2024 > June > Exploit Attempts Recorded Against New MOVEit Transfer Vulnerability - Patch ASAP!
2024-06-26 14:57
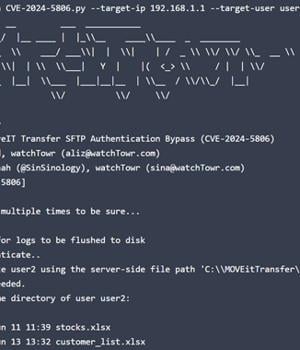
A newly disclosed critical security flaw impacting Progress Software MOVEit Transfer is already seeing exploitation attempts in the wild shortly after details of the bug were publicly disclosed. The vulnerability, tracked as CVE-2024-5806 (CVSS score: 9.1), concerns an authentication bypass that impacts the following versions - From 2023.0.0 before 2023.0.11 From 2023.1.0 before 2023.1.6, and&
News URL
https://thehackernews.com/2024/06/new-moveit-transfer-vulnerability-under.html
Related news
- Zero-Day Alert: Google Releases Chrome Patch for Exploit Used in Russian Espionage Attacks (source)
- CrushFTP: Patch critical vulnerability ASAP! (CVE-2025-2825) (source)
- BlackLock Ransomware Exposed After Researchers Exploit Leak Site Vulnerability (source)
- PipeMagic Trojan Exploits Windows Zero-Day Vulnerability to Deploy Ransomware (source)
- Critical Erlang/OTP SSH pre-auth RCE is 'Surprisingly Easy' to exploit, patch now (source)
- Critical Erlang/OTP SSH RCE bug now has public exploits, patch now (source)
- Kimsuky Exploits BlueKeep RDP Vulnerability to Breach Systems in South Korea and Japan (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2024-06-25 | CVE-2024-5806 | Unspecified vulnerability in Progress Moveit Transfer Improper Authentication vulnerability in Progress MOVEit Transfer (SFTP module) can lead to Authentication Bypass.This issue affects MOVEit Transfer: from 2023.0.0 before 2023.0.11, from 2023.1.0 before 2023.1.6, from 2024.0.0 before 2024.0.2. | 9.8 |