Security News > 2023 > August > Experts Uncover How Cybercriminals Could Exploit Microsoft Entra ID for Elevated Privilege
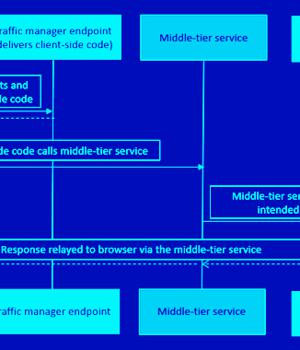
Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID application by taking advantage of an abandoned reply URL. "An attacker could leverage this abandoned URL to redirect authorization codes to themselves, exchanging the ill-gotten authorization codes for access tokens," Secureworks Counter Threat Unit said in a technical report published last week.
Reply URL, also called redirect URI, refers to the location where the authorization server sends the user once the app has been successfully authorized and granted an authorization code or access token.
"The authorization server sends the code or token to the redirect URI, so it's important you register the correct location as part of the app registration process," Microsoft notes in its documentation.
Secureworks CTU said it identified an abandoned Dynamics Data Integration app reply URL associated with the Azure Traffic Manager profile that made it possible to invoke the Power Platform API via a middle-tier service and tamper with the environment configurations.
This banks on the possibility that a victim clicks on a malicious link, as a result of which the authorization code issued by Microsoft Entra ID upon logging is delivered to a redirect URL hijacked by the threat actor.
The disclosure comes as Kroll revealed an uptick in DocuSign-themed phishing campaigns utilizing open redirects, enabling adversaries to propagate specially crafted URLs that, when clicked, redirect potential victims to a malicious site.
News URL
https://thehackernews.com/2023/08/experts-uncover-how-cybercriminals.html
Related news
- When confusion becomes a weapon: How cybercriminals exploit economic turmoil (source)
- Russian Hackers Exploit Microsoft OAuth to Target Ukraine Allies via Signal and WhatsApp (source)
- How cybercriminals exploit psychological triggers in social engineering attacks (source)
- Hackers exploit VMware ESXi, Microsoft SharePoint zero-days at Pwn2Own (source)